An engineer must implement a solution on a Cisco ASR 1000 Series router to protect against DDoS attacks. DDoS traffic must be dropped by transmitting Flowspec attributes to edge routers, instructing them to generate an ACL via class-maps and policy-maps. The engineer already configured BGP neighbors. Which action must be taken next?

Refer to the exhibit. An engineer must configure an IPsec VPN connection between site 1 and site 2. The ISAKMP policy for the phase 1 negotiations of the tunnel must use AES and SHA-256. This configuration was applied to both PE routers; however, the tunnel fails to come up:
crypto isakmp policy 10
encryption 3des
hash md5
authentication pre-share
group 12
Which two commands must be run on router PE1 to resolve the issue? (Choose two.)
An engineer must configure NTP servers in Cisco Enterprise NFVIS. The primary NTP server has an IP address of 192.168.1.1 and the backup NTP server has an IP address of 192.168.2.1. Which two commands must be run to complete the configuration? (Choose two.)
An engineer must add VNF implementation definitions and VNF service definitions to an OpenStack deployment data model to deploy virtual routers and firewalls to an enterprise network. After the virtual machine resources are prepared, which action must be taken next?
What does Cisco Always-On Cloud DDoS use to protect against DDoS attacks?
How does SR-IOV move data directly to and from the network adapter?
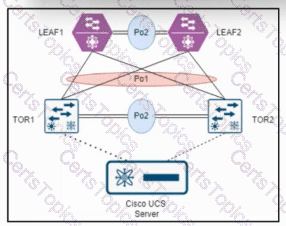
Refer to the exhibit. An engineer must connect switch TOR1 and switch TOR2 to switch LEAF1 and switch LEAF2 by using double-sided vPCs. LEAF1 and LEAF2 are already configured as vPC peers. Which action must be taken next to complete the configuration?
An engineer must create a new VPC and deploy several Amazon EC2 instances in AWS. Only SSH connections originating from IP address 20.20.20.20 must be allowed to reach the EC2 instances. What must be configured?
What is a benefit of using VXLANs in a cloud-scale environment?
How does SR-IOV move data directly to and from the network adapter?

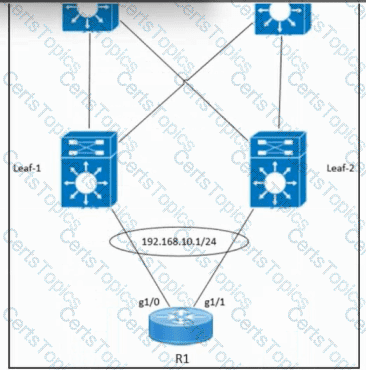
Refer to the exhibit. An engineer must configure EVPN port-active multihoming on router R1. Which command must be run against the g1/0 and g1/1 interfaces on R1 to complete the physical Ethernet bundle for multihoming on a host named Host-1?
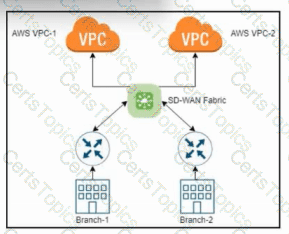
Refer to the exhibit. An engineer must design a solution that allows a user to choose which private Cisco Catalyst SD-WAN network they want to connect to AWS. The solution must automatically identify the AWS VPC and other cloud services based on the user credentials. What must be used?
What is a valid connection method between carrier-neutral facilities within the same metro area?
What is a valid connection method between carrier-neutral facilities that are more than 20 miles away from each other?
A network architect must design a solution for implementing virtualization functions. The main goal is to ensure network reliability and reduce downtime by considering the network operational team's requirements:
The solution must providereal-time network-state visibility.
The solution must supportautomated rollback in the event of configuration errors.
The solution must allowefficient troubleshooting and diagnostics.
Which action must the team take to achieve the goal?
An engineer must design a high-availability solution that provides path redundancy for IP by allowing redundant gateways to share MAC protocols and addresses. A group of Layer 3 routers must be allowed to share the default gateway on a LAN, load balance, and seamlessly take over the traffic transfer role if a router in the group fails. What must be used?
How does log management assist in meeting the requirements of cloud security regulatory compliance?

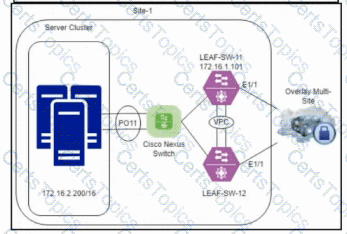
Refer to the exhibit. An engineer is troubleshooting an issue with switch LEAF-SW-11. The engineer observes that several main servers on the VXLAN BGP EVPN Multi-Site network experience 50–60% packet loss inbound and outbound, and all the DCI tracking interfaces are down. Which two actions must be taken to resolve the issue? (Choose two.)