Which two Network Discover/Cloud Storage targets apply Information Centric Encryption as policy response rules?
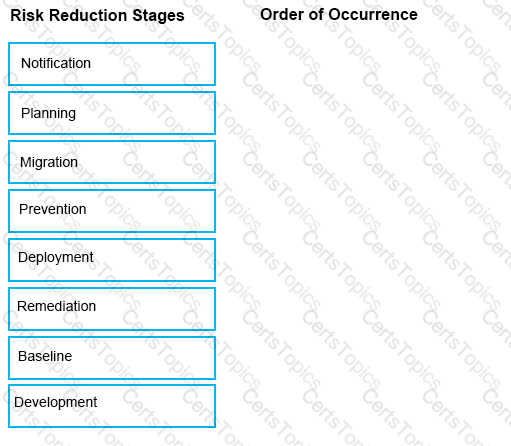
The Symantec Data Loss risk reduction approach has six stages.
Drag and drop the six correct risk reduction stages in the proper order of Occurrence column.
How should a DLP administrator change a policy so that it retains the original file when an endpoint incident has detected a “cope to USB device” operation?
Which action is available for use in both Smart Response and Automated Response rules?
What detection technology supports partial contents matching?
Which service encrypts the message when using a Modify SMTP Message response rule?
A customer needs to integrate information from DLP incidents into external Governance, Risk and Compliance dashboards.
Which feature should a third party component integrate with to provide dynamic reporting, create custom incident remediation processes, or support business processes?
Which two detection technology options run on the DLP agent? (Choose two.)
Which network Prevent action takes place when the network Incident list shows the message is “Modified”?
An organization wants to restrict employees to copy files only a specific set of USB thumb drives owned by the organization.
Which detection method should the organization use to meet this requirement?