You work as a security manager for BlueWell Inc. You are going through the NIST SP 800-37 C&A methodology, which is based on four well defined phases. In which of the following phases of NIST SP 800-37 C&A methodology does the security categorization occur?
Which of the following is a standard that sets basic requirements for assessing the effectiveness of computer security controls built into a computer system?
Which of the following security models characterizes the rights of each subject with respect to every object in the computer system?
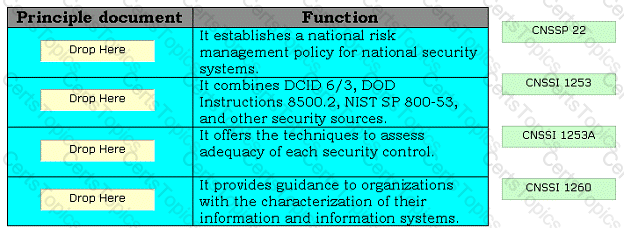
Drag and drop the appropriate principle documents in front of their respective functions.