You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to
configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)
Regarding IPsec CoS-based VPNs, what is the number of IPsec SAs associated with a peer based upon?
Exhibit.
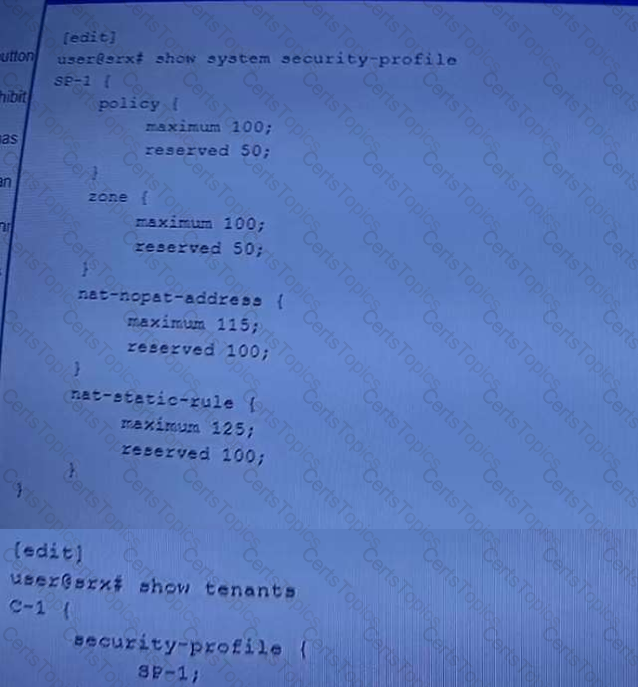
Referring to the exhibit, which two statements are true? (Choose two.)
Click the Exhibit button.
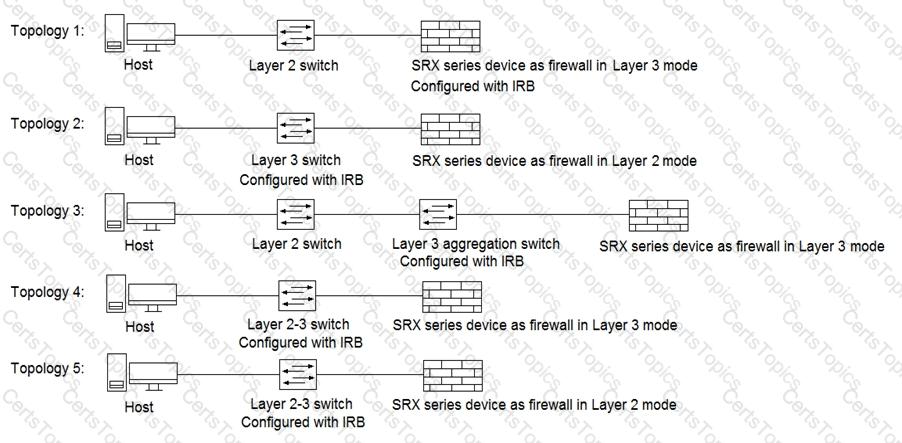
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)