On which server should you install the Azure ATP sensor?
You need to meet the Intune requirements for the Windows 10 devices.
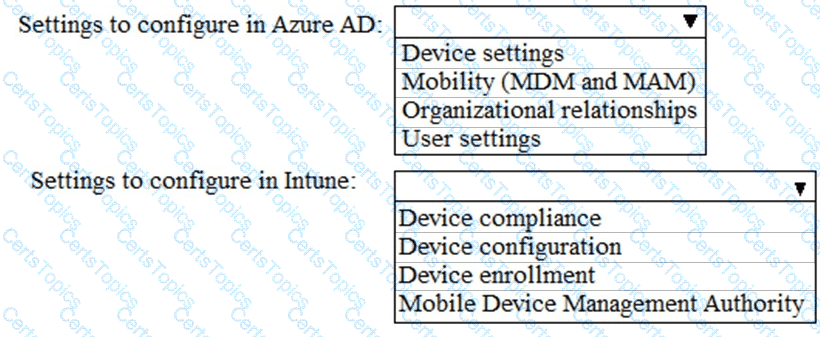
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
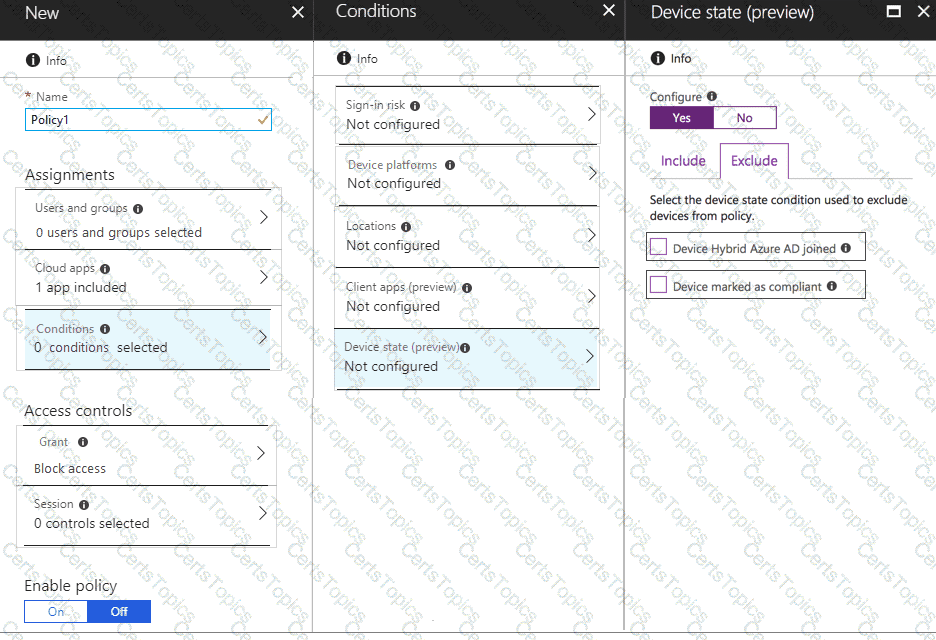
You need to configure a conditional access policy to meet the compliance requirements.
You add Exchange Online as a cloud app.
Which two additional settings should you configure in Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to ensure that User1 can enroll the devices to meet the technical requirements. What should you do?