How does sandboxing help with the analysis of malware?
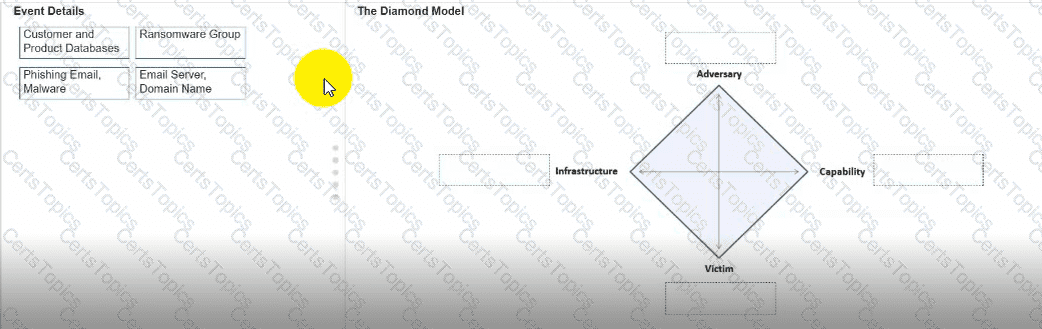
You need to diagram an intrusion event by using the Diamond Model.
Move each event detail from the list on the left to the correct location in the diagram on the right.
Note: You will receive partial credit for each correct response.
You work for a hospital that stores electronic protected health information (ePHI) in an online portal. Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees’ mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?