A network administrator has deployed the following (partial) configuration:
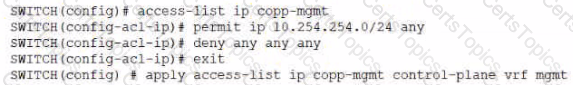
What is the effect of this policy?
The example ACL is used with Aruba CX 6400 switches to permit traffic to web servers configured on interface 1/1/1 inbound with IP 10.254.4.1/24.
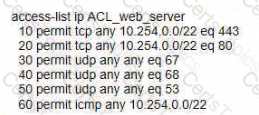
How does this ACL affect the HTTPS traffic to destination 10.254.4.7 from a client 10.253.1.5 via interface 1/1/2 with IP 10 254.3.1/24?
You have removed a member out of the ArubaOS-CX 6300 VSF configuration. The login to the removed member falls. What is true about switch login recovery?
A customer with an ArubaOS-CX 6300M switch is having a performance issue on the network and has received complaints about users experiencing intermittent connectivity. After performing troubleshooting it is determined that many of the local websites on the LAN that users are unable to reach are resolved to an invalid MAC address.
What are the minimum steps that should be performed to mitigate this condition? (Select two)