An Administrator is alerted to a Suspicious Process Creation security event from multiple users.
The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
How many use cases should a POC success criteria document include?
An administrator has a critical group of systems running Windows XP SP3 that cannot be upgraded The administrator wants to evaluate the ability of Traps to protect these systems and the word processing applications running on them
How should an administrator perform this evaluation?
A customer has purchased Cortex XDR and requires phone support for the product.
Which Palo Alto Networks offering would fulfill this need?
An adversary is attempting to communicate with malware running on your network for the purpose of controlling malware activities or for ex filtrating data from your network. Which Cortex XDR Analytics alert is this activity most likely to trigger'?
Which Cortex XDR capability prevents running malicious files from USB-connected removable equipment?
What is the difference between the intel feed’s license quotas of Cortex XSOAR Starter Edition and Cortex XSOAR (SOAR + TIM)?
The certificate used for decryption was installed as a trusted root CA certificate to ensure communication between the Cortex XDR Agent and Cortex XDR Management Console What action needs to be taken if the administrator determines the Cortex XDR Agents are not communicating with the Cortex XDR Management Console?
What is the requirement for enablement of endpoint and network analytics in Cortex XDR?
Given the integration configuration and error in the screenshot what is the cause of the problem?
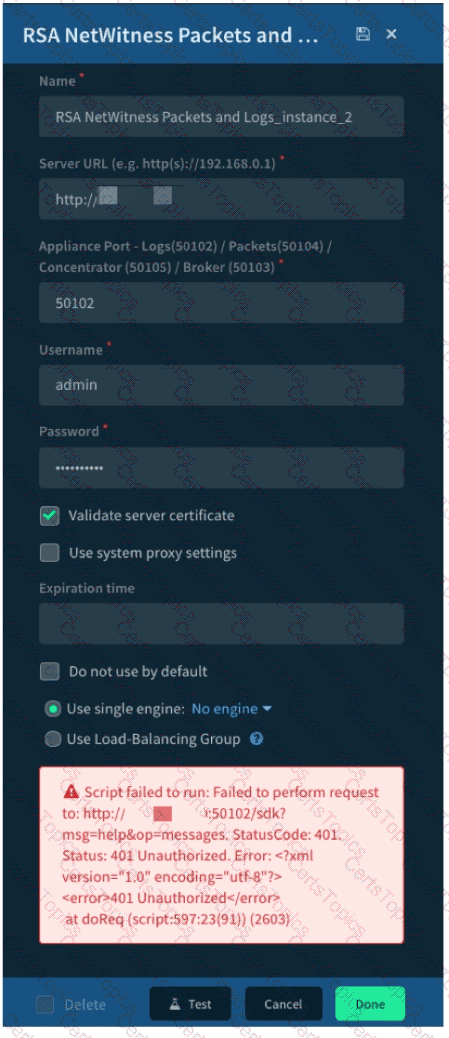
Which feature of Cortex XSIAM helps analyst reduce the noise and false positives that often plague traditional SIEM systems?
Which two filter operators are available in Cortex XDR? (Choose two.)
An administrator of a Cortex XDR protected production environment would like to test its ability to protect users from a known flash player exploit.
What is the safest way to do it?
When initiated, which Cortex XDR capability allows immediate termination of the process-or entire process tree-on an anomalous process discovered during investigation of a security event?
Which consideration should be taken into account before deploying Cortex XSOAR?
What are process exceptions used for?
Which two types of lOCs are available for creation in Cortex XDR? (Choose two.)
An EDR project was initiated by a CISO. Which resource will likely have the most heavy influence on the project?
A customer has 2700 endpoints. There is currently concern about recent attacks in their industry and threat intelligence from a third-party subscription. In an attempt to be proactive, phishing simulations have been prioritized, but the customer wants to gain more visibility and remediation capabilities specific to their network traffic.
Which Cortex product provides these capabilities?
When preparing for a Cortex XSOAR proof of value (POV), which task should be performed before the evaluation is requested?
A General Purpose Dynamic Section can be added to which two layouts for incident types? (Choose two)
Which Cortex XDR Agent capability prevents loading malicious files from USB-connected removable equipment?
Which two Cortex XSOAR incident type features can be customized under Settings > Advanced > Incident Types? (Choose two.)
Which action should be performed by every Cortex Xpanse proof of value (POV)?
Which two filter operators are available in Cortex XDR? (Choose two.)
What is the recommended first step in planning a Cortex XDR deployment?
Cortex XSOAR has extracted a malicious IP address involved in command-and-control traffic.
What is the best method to automatically block this IP from communicating with endpoints without requiring a configuration change on the firewall?
Which statement applies to the malware protection flow of the endpoint agent in Cortex XSIAM?
The customer has indicated they need EDR data collection capabilities, which Cortex XDR license is required?
Which Cortex XDR license is required for a customer that requests endpoint detection and response (EDR) data collection capabilities?
Which statement applies to the differentiation of Cortex XDR from security information and event management (SIEM)?
Which command-line interface (CLI) query would retrieve the last three Splunk events?
Which two log types should be configured for firewall forwarding to the Cortex Data Lake for use by Cortex XDR? (Choose two)
How does DBot score an indicator that has multiple reputation scores?
What are the key capabilities of the ASM for Remote Workers module?
Which Linux OS command will manually load Docker images onto the Cortex XSOAR server in an air-gapped environment?
A Cortex XSOAR customer has a phishing use case in which a playbook has been implemented with one of the steps blocking a malicious URL found in an email reported by one of the users.
What would be the appropriate next step in the playbook?
Within Cortex XSIAM, how does the integration of Attack Surface Management (ASM) provide a unified approach to security event management that traditional SIEMs typically lack?
What is the result of creating an exception from an exploit security event?
Which feature in Cortex XSIAM extends analytics detections to all mapped network and authentication data?
Which two formats are supported by Whitelist? (Choose two)
What is the primary function of an engine in Cortex XSOAR?
What is the primary mechanism for the attribution of attack surface data in Cortex Xpanse?
Which resource can a customer use to ensure that the Cortex XDR agent will operate correctly on their CentOS 07 servers?
What allows the use of predetermined Palo Alto Networks roles to assign access rights to Cortex XDR users?
A customer has purchased Cortex XSOAR and has a need to rapidly stand up the product in their environment. The customer has stated that their internal staff are currently occupied with other projects.
Which Palo Alto Networks service offering should be recommended to the customer?
Which CLI query would bring back Notable Events from Splunk?
A)
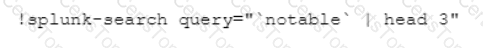
B)
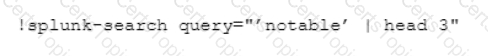
C)
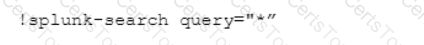
D)
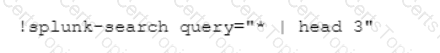
An adversary attempts to communicate with malware running on a network in order to control malware activities or to exfiltrate data from the network.
Which Cortex XDR Analytics alert will this activity most likely trigger?
If you have a playbook task that errors out. where could you see the output of the task?
Which task setting allows context output to a specific key?