Which two methods can be configured to validate the revocation status of a certificate? (Choose two)
The administrator has enabled BGP on a virtual router on the Palo Alto Networks NGFW, but new routes do not seem to be populating the virtual router.
Which two options would help the administrator Troubleshootthis issue? (Choose two.)
What will be the egress interface if the traffic’s ingress interface is Ethernet 1/6 sourcing form 192.168.11.3 and to the destination 10.46.41.113.during the.
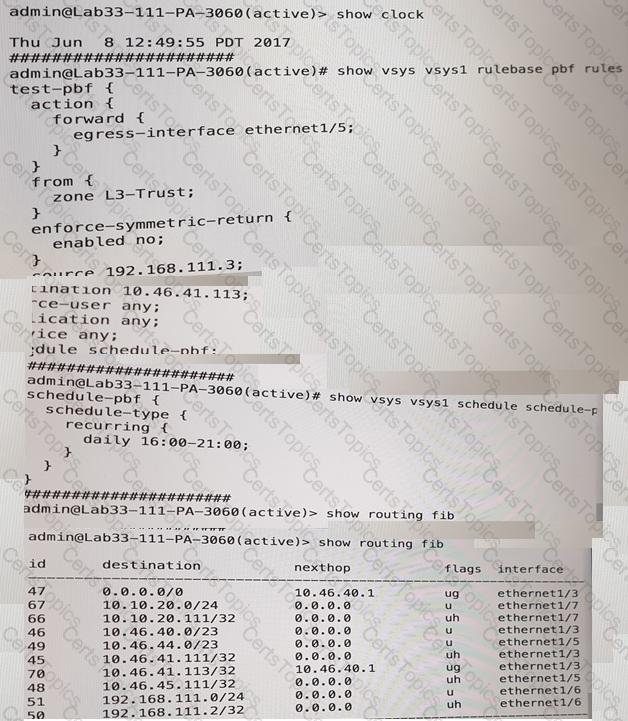
A user's traffic traversing a Palo Alto Networks NGFW sometime can reach http//www company com At the session times out. The NGFW has been configured with a PBF rule that the user's traffic matches when it goes to http //www company com.
How con the firewall be configured to automatically disable the PBF rule if thenext hop goes down?
Which three authentication faction factors does PAN-OS® software support for MFA? (Choose three.)
In High Availability, which information is transferred via the HA data link?
Which two action would be part of an automatic solution that would block sites with untrusted certificates without enabling SSLforward proxy? (Choose two.)
What are two benefits of nested device groups in panorama?(Choose two )
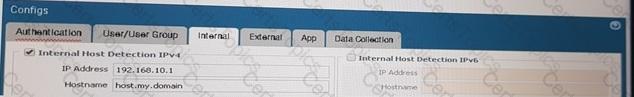
View theGlobalProtect configuration screen capture.
What is the purpose of this configuration?
An administrator needs to optimize traffic to prefer business-critical applications overnon-critical applications.
QoS natively integrates with which feature to provide service quality?
Refer to the exhibit.
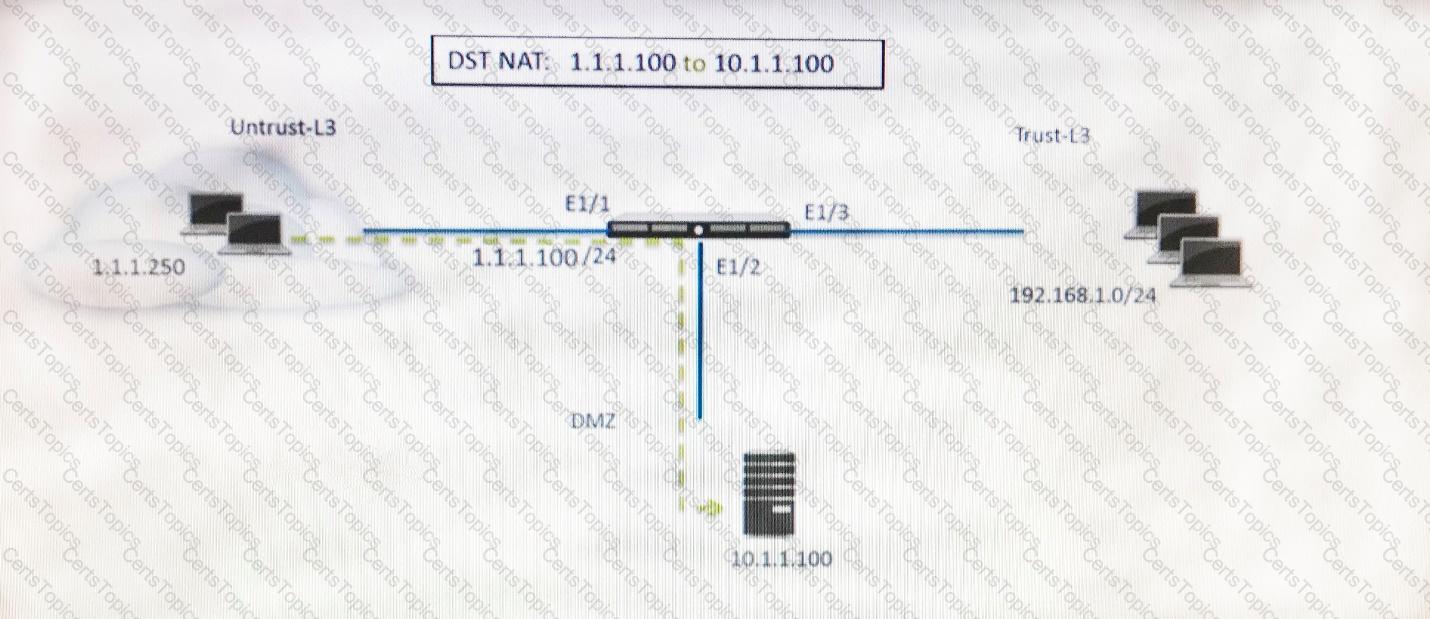
A web server in the DMZ is being mapped to a public address through DNAT.
Which Security policy rule will allow traffic to flow to the web server?