Console is running in a Kubernetes cluster, and Defenders need to be deployed on nodes within this cluster.
How should the Defenders in Kubernetes be deployed using the default Console service name?
Given this information:
The Console is located at The username is: cluster
The password is: password123
The image to scan is: myimage:latest
Which twistcli command should be used to scan a Container for vulnerabilities and display the details about each vulnerability?
Which Defender type performs registry scanning?
You are tasked with configuring a Prisma Cloud build policy for Terraform. What type of query is necessary to complete this policy?
An administrator wants to retrieve the compliance policies for images scanned in a continuous integration (CI) pipeline.
Which endpoint will successfully execute to enable access to the images via API?
If you are required to run in an air-gapped environment, which product should you install?
Which three options for hardening a customer environment against misconfiguration are included in Prisma Cloud Compute compliance enforcement for hosts? (Choose three.)
What is the default namespace created by Defender DaemonSet during deployment?
During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in their environment.
Which statement correctly describes the default vulnerability policy?
Which two statements apply to the Defender type Container Defender - Linux?
Which policy type in Prisma Cloud can protect against malware?
Which two of the following are required to be entered on the IdP side when setting up SSO in Prisma Cloud? (Choose two.)
Which categories does the Adoption Advisor use to measure adoption progress for Cloud Security Posture Management?
Which two offerings will scan container images in Jenkins pipelines? (Choose two.)
An administrator has access to a Prisma Cloud Enterprise.
What are the steps to deploy a single container Defender on an ec2 node?
The security team wants to enable the “block” option under compliance checks on the host.
What effect will this option have if it violates the compliance check?
What is the function of the external ID when onboarding a new Amazon Web Services (AWS) account in Prisma Cloud?
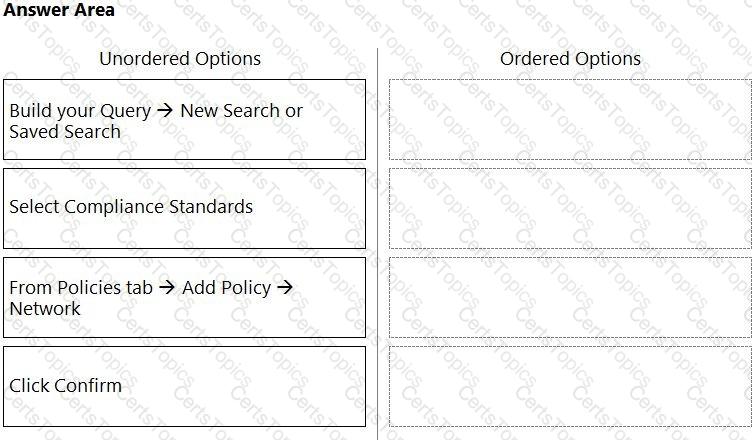
What is the order of steps to create a custom network policy?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
A customer has a requirement to scan serverless functions for vulnerabilities.
Which three settings are required to configure serverless scanning? (Choose three.)
What is the most reliable and extensive source for documentation on Prisma Cloud APIs?
Which two integrations enable ingesting host findings to generate alerts? (Choose two.)
Which two services require external notifications to be enabled for policy violations in the Prisma Cloud environment? (Choose two.)
What is the maximum number of access keys a user can generate in Prisma Cloud with a System Admin role?
Which “kind” of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
How many CLI remediation commands can be added in a custom policy sequence?
An organization wants to be notified immediately to any “High Severity” alerts for the account group “Clinical Trials” via Slack.
Which option shows the steps the organization can use to achieve this goal?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
Where can a user submit an external new feature request?
A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer’s request?
What factor is not used in calculating the net effective permissions for a resource in AWS?
Which data security default policy is able to scan for vulnerabilities?
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
Prisma Cloud Compute has been installed on Onebox. After Prisma Cloud Console has been accessed. Defender is disconnected and keeps returning the error "No console connectivity" in the logs.
What could be causing the disconnection between Console and Defender in this scenario?
A customer wants to monitor its Amazon Web Services (AWS) accounts via Prisma Cloud, but only needs the resource configuration to be monitored at present.
Which two pieces of information are needed to onboard this account? (Choose two.)
Which of the following is not a supported external integration for receiving Prisma Cloud Code Security notifications?
Which role must be assigned to DevOps users who need access to deploy Container and Host Defenders in Compute?
Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernetes deployment? (Choose two.)
Which of the following are correct statements regarding the use of access keys? (Choose two.)
A customer has a requirement to automatically protect all Lambda functions with runtime protection. What is the process to automatically protect all the Lambda functions?
Which two filters are available in the SecOps dashboard? (Choose two.)
Prisma Cloud supports which three external systems that allow the import of vulnerabilities and provide additional context on risks in the cloud? (Choose three.)
Which set of steps is the correct process for obtaining Console images for Prisma Cloud Compute Edition?
What is the correct method for ensuring key-sensitive data related to SSNs and credit card numbers cannot be viewed in Dashboard > Data view during investigations?
An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default policy “AWS S3 buckets are accessible to public”. The policy definition follows:
config where cloud.type = 'aws' AND api.name='aws-s3api-get-bucket-acl' AND json.rule="((((acl.grants[? (@.grantee=='AllUsers')] size > 0) or policyStatus.isPublic is true) and publicAccessBlockConfiguration does not exist) or ((acl.grants[?(@.grantee=='AllUsers')] size > 0) and publicAccessBlockConfiguration.ignorePublicAcis is false) or (policyStatus.isPublic is true and publicAccessBlockConfiguration.restrictPublicBuckets is false)) and websiteConfiguration does not exist"
Why did this alert get generated?
Based on the following information, which RQL query will satisfy the requirement to identify VM hosts deployed to organization public cloud environments exposed to network traffic from the internet and affected by Text4Shell RCE (CVE-2022-42889) vulnerability?
• Network flow logs from all virtual private cloud (VPC) subnets are ingested to the Prisma Cloud Enterprise Edition tenant.
• All virtual machines (VMs) have Prisma Cloud Defender deployed.
A)
B)
C)
D)
Which port should a security team use to pull data from Console’s API?
A customer wants to be notified about port scanning network activities in their environment. Which policy type detects this behavior?
Which Prisma Cloud policy type can protect against malware?
Which data storage type is supported by Prisma Cloud Data Security?
When configuring SSO how many IdP providers can be enabled for all the cloud accounts monitored by Prisma Cloud?
A DevOps lead reviewed some system logs and notices some odd behavior that could be a data exfiltration attempt. The DevOps lead only has access to vulnerability data in Prisma Cloud Compute, so the DevOps lead passes this information to SecOps.
Which pages in Prisma Cloud Compute can the SecOps lead use to investigate the runtime aspects of this attack?
Which statement accurately characterizes SSO Integration on Prisma Cloud?
A customer wants to turn on Auto Remediation.
Which policy type has the built-in CLI command for remediation?
Given the following audit event activity snippet:
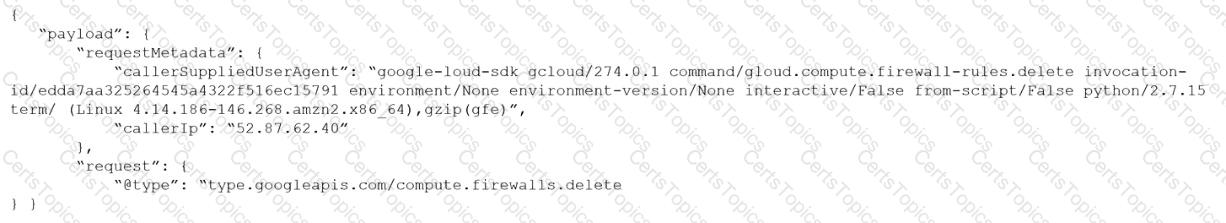
Which RQL will be triggered by the audit event?
A)
B)
C)
D)
An administrator for Prisma Cloud needs to obtain a graphical view to monitor all connections, including connections across hosts and connections to any configured network objects.
Which setting does the administrator enable or configure to accomplish this task?
Which two CI/CD plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.).
While writing a custom RQL with array objects in the investigate page, which type of auto-suggestion a user can leverage?
Given a default deployment of Console, a customer needs to identify the alerted compliance checks that are set by default.
Where should the customer navigate in Console?
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
Prisma Cloud cannot integrate which of the following secrets managers?
A Prisma Cloud Administrator onboarded an AWS cloud account with agentless scanning enabled successfully to Prisma Cloud. Which item requires deploying defenders to be able to inspect the risk on the onboarded AWS account?
Which policy type provides information about connections from suspicious IPs in a customer database?
Which statement about build and run policies is true?
Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?
Which serverless cloud provider is covered by the "overly permissive service access" compliance check?
In Azure, what permissions need to be added to Management Groups to allow Prisma Cloud to calculate net effective permissions?
Which container image scan is constructed correctly?
The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
Which role does Prisma Cloud play when configuring SSO?
What is an example of an outbound notification within Prisma Cloud?
When would a policy apply if the policy is set under Defend > Vulnerability > Images > Deployed?
A customer has Defenders connected to Prisma Cloud Enterprise. The Defenders are deployed as a DaemonSet in OpenShift.
How should the administrator get a report of vulnerabilities on hosts?
Which three types of classifications are available in the Data Security module? (Choose three.)
What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon Web Services (AWS) cloud accounts are being used? (Choose two.)
Given the following information, which twistcli command should be run if an administrator were to exec into a running container and scan it from within using an access token for authentication?
• Console is located at
• Token is: TOKEN_VALUE
• Report ID is: REPORTJD
• Container image running is: myimage:latest
Which of the below actions would indicate – “The timestamp on the compliance dashboard?
The attempted bytes count displays?