Which change can be made on a cluster with software-based Data-at-Rest Encryption enabled?
In the event of a disk failure, which process will immediately ad automatically scans Cassandra to find all data previously hosted on the failed disk, and all disks in that node?
An administrator is performing validation testing of a new-deploy cluster. During this test, the administrator disconnect each LAN interface from each of the nodes while pinging the hypervisor and guest VMs.
When the first interface is disconnected, pings continue as expected to the hypervisor, but pings stop responding from the guest. Pings continue when the interface is reconnected. When the second interface is disconnected, pings continue to both the hypervisor and guest VMs.
What could be the cause of this error?
An administrator needs to configure Prism to send encrypted messages to a set of recipients.
Which setting must be applied?
How will an HDD failure affect VMs with data on the failed device?
Which best practice should be followed when creating a bond in a Nutanix cluster?
Microsegmentation was recently enabled in a Nutanix environment. The administrator wants to leverage Prism Central to create a policy that will block all traffic regardless of direction, between two groups of VMs identified by their category.
Which policy should be used to meet this requirement?
An administrator needs to run a mixed Exchange and SQL workload with a guaranteed amount of container
space for each application.
How should the administrator meet this requirement?
An administrator is setting up a Nutanix cluster and needs to configure the default VLAN.
Which configuration should the administrator choose?
When installing Nutanix Guest Tools (NGT) on an ESXi-hosted VM, which port should be enabled on the VM to allow communication with the NGT-Controller VM service?
The customer is seeing high memory utilization on a mission critical VM. Users report that the application is unavailable. The guest OS does not support hot add components.
How should the administrator fix this issue?
An Administrator has been asked to deploy VMs using a specific image. The image has been configured with settings and applications that will be used by engineering to develop a new product by the company.
The image is not available on the desired cluster, but it is available in other cluster associated with Prism Central.
Why isno’t the image available?
An administrator needs to shut down an AHV cluster to relocate hardware. The administrator upgrades NCC and runs health checks.
Which steps should the administrator perform next?
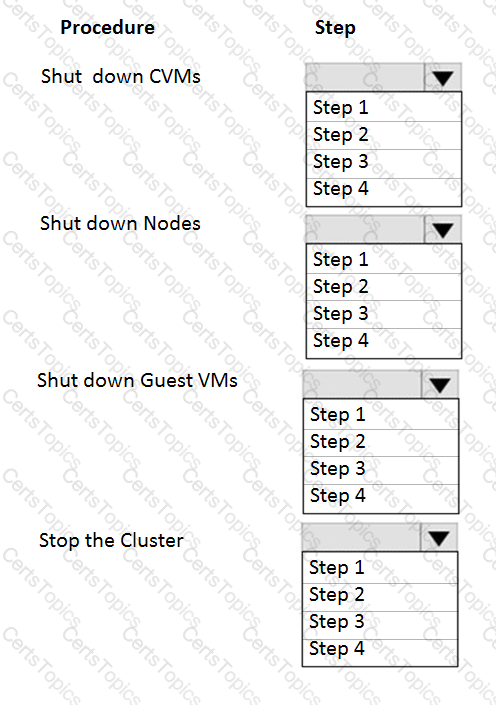
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements.
Refer to the Exhibit:
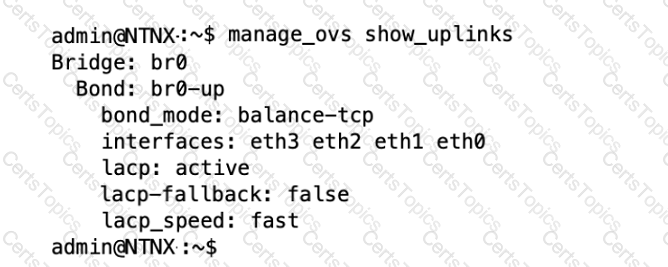
An administrator is adding a new node to a cluster. The node has been imaged to the same versions of AHV and AOS that the cluster is
running, configured with appropriate IP addresses, and br0-up has been configured in the same manner as the existing uplink bonds.
When attempting to add the node to the cluster with the Expand Cluster function in Prism, the cluster is unable to find the new node.
Based on the above output from the new node, what is most likely the cause of this issue?
Refer to Exhibit:
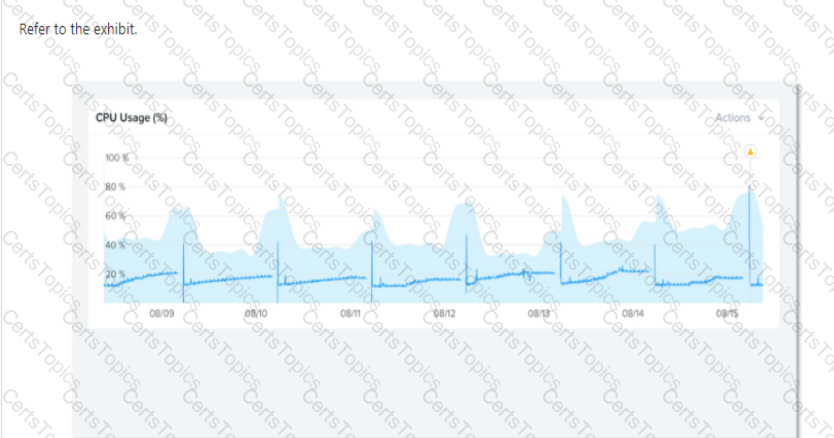
Why has an anomaly been triggered?
An administrator is tasked with configuring networking on an AHV cluster and needs to optimize for maximum single VM throughput.
Which bond mode should the administrator select?
In Files, how many FSVMs are deployed by default?
Which capability refers to the storage of VM data on the node where the VM is running and ensure that the read I/O does not have to traverse the network?
After the initial configuration and upgrade of NCC, the administrator notices these critical alerts:
. IPMI 10.7.133.33 is using default password
. Host 10.7.133.25 is using default password
. CVM 10.7.133.31 is using default password
Which two initial cluster configuration tasks were missed during the deployment process? (Choose two.)
An administrator manages an AHV cluster that is dedicated to a dev/test environment. The administrator receiving complaints from users that they are unable to create new VMs on the cluster.
After the reviewing the cluster, the administrator finds that the memory resources are almost fully utilized, with many VMs over-provisioned on memory.
What option is the most efficient resolution to enable additional VMs to be created?
What is Prism Central primarily used for?
After deploying a cluster, time is not synchronizing properly.
What task needs to be performed?
In which two scenarios is Native Key Management Server supported? (Choose two)
Which command should an administrator run from the CLI to view the uplink state of all AHV nodes in the
cluster?
Refer to Exhibit:
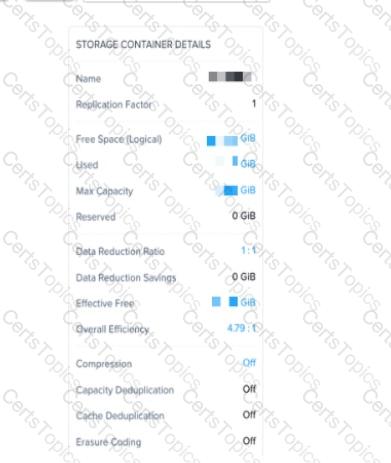
An administrator needs to enable inline deduplication for a pre-existing storage container. When trying to enable deduplication on the storage container. this feature is grayed-out.
What is the reason for this behavior?
An administrator is tasked with configuring network on an AHV cluster and wants to maximize throughput for the host with many small VMs while minimizing network switch configuration.
Which bond mode should the administrator select?
An administrator needs to deploy an application with a large amount of data connected via Nutanix volumes.
Which two actions should the administrator take when designing the Volume Group? (Choose two.)
What is the expected behavior of the VMs residing on that host when a controller VM becomes unavailable?
A Nutanix cluster is equipped with four nodes. Four VMs on this cluster have been configured with a VM-VM anti-affinity policy and are each being hosted by a different node.
What occurs to the cluster and these VMs during an AHV upgrade?
A newly-hired Nutanix administrator was tasked by the CIO to create a single VM on a test network. The network administrator stated that a native VLAN was used on the Cisco TOR switches with the following parameters:
IP address:172,16.1.2
Network Mask: 255.255.255.0
Default gateway: 172.16.1.1
VLAN:1
The same parameters were used to create a network profile on Nutanix, but the when the VM was on …
What should the Nutanix administrator do to fix this issue?
An administrator recently added new SSDs to a Nutanix cluster and knows the firmware will be out of date, Due to security constraints, the cluster does not have access to the Internet.
Which two steps must be completed to update the firmware? (Choose two.)
In which two scenarios is an automated live migration likely to occur? (Choose two)
On a Nutanix cluster, what does Network Segmentation refer to?
Refer to Exhibit:
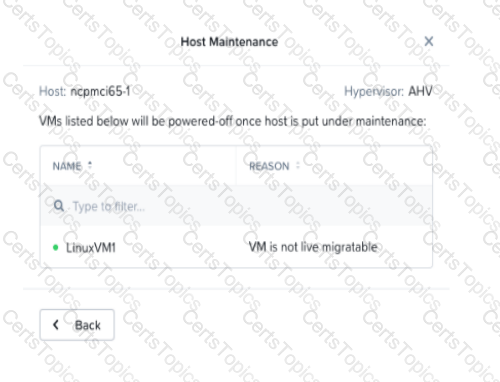
An administrator is trying to put a node into maintenance mode but receives the message shown in the exhibit.
What is a potential reason for this dialog?
A customer has a 24-node cluster with all containers configured with RF3. Two different nodes have incurred a simultaneous HDD failure.
What is the result?
What is the name of the internal bridge used by AHV nodes and CVMs?
An administrator notices that most of the VMs in the cluster are on one host. Users report that an application seems to respond slowly. The application server VM has significantly more memory assigned to it than other VMs.
How should the administrator fix this issue?
Which component can be associated with a storage policy?
In Nutanix clusters, which feature ensures VMs can be migrated and restarted on another host in case of failure?
An administrator has been tasked with increasing security on Nutanix cluster by disabling password authentication when accessing the CVM and AHV hosts and instead moving to key-based SSH,
What is the easiest way for the administrator to meet these needs?
How should an administrator configure a custom alert for a specific VM in Prism?
The Stargate service becomes unavailable on a single CVM on an AHV node. What is used to maintain I/O operations in the cluster?
An administrator wants to reduce the largest amount of alert emails received from Prism Central.
Which two settings should the administrator customize to meet this requirement? (Choose two)
How should an administrator enable secure access to Volumes using a password?
Which three upgrades should an administrator be able to perform using Lifecycle Management? (Choose Three)
An administrator has been alerted to a VM that has high I/O latency and wants to determine if there are any other factors, such as insufficient network or memory resources that correlate, as part of a troubleshooting process.
Which type of chart should the administrator create to allow all relevant data to be easily exported to CSV for later analysis?
Refer to Exhibit:
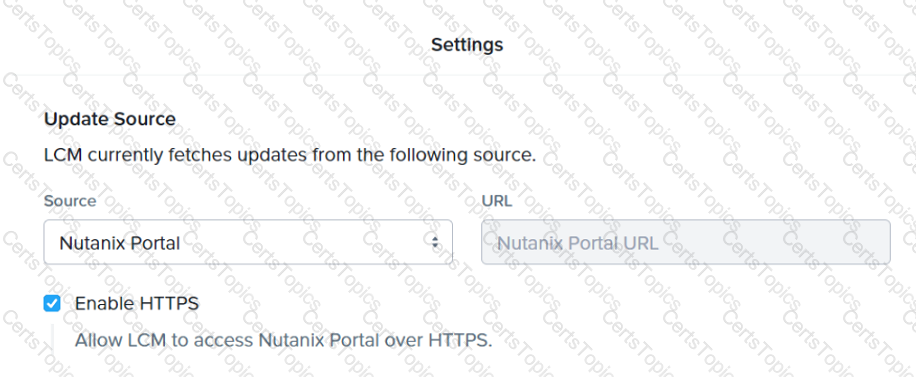
The Update Source for LCM has been configured as shown in the exhibit. Inventory is failing consistently.
What is the likely cause of this issue?
An administrator manages a cluster and notices several failed components shown in the exhibit.

What two options does the administrator have to run all NCC checks manually? (Choose two.)
Which two capabilities does IPAM provide in a Nutanix networking configuration? (Choose two.)
An administrator needs to configure a new subnet on an AHV cluster and want to ensure that VMs will automatically be assigned an IP address at creation time.
Which type of network does the administrator need to create?
An administrator responsible for a VDl environment needs to investigate reports of slow logins. The administrator finds that increasing the number of vCPUs from 2 to 4 will reduce the login times. Production workloads are consuming 75% of the host CPU on the cluster. The administrator increases the vCPU count on all of the VDl VMs.
What are two impacts on the cluster? (Choose two)
Refer to the exhibit.
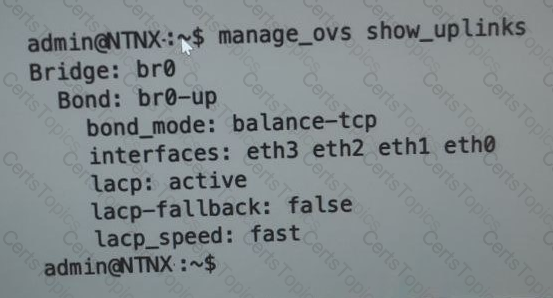
An administrator is adding a new node to a cluster. The node has been imaged to the same versions of AHV and AOS that the cluster running, configured with appropriate IP addresses, and br0-up has been configured the same the existing uplink bonds
When attempting to add the node to the cluster with the Expand Cluster function in Prism , the cluster is unable to find the new node.
Based on the above output from the new node, what is most likely the cause of this issue?
What are two minimum prerequisites for live migration to succeed? (Choose two.)