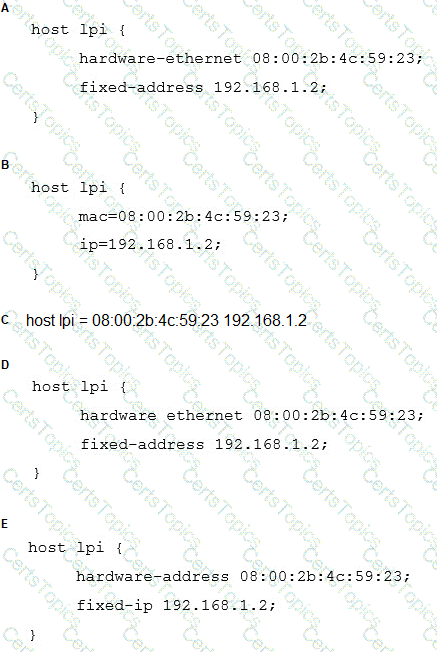
A host, called lpi, with the MAC address 08:00:2b:4c:59:23 should always be given the IP address of 192.168.1.2 by a DHCP server running ISC DHCPD.
Which of the following configurations will achieve this?
In order to join a file server to the Active Directory domain intra.example.com, the following smb.conf has been created:
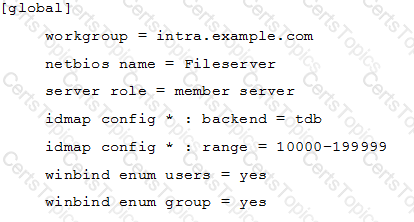
The command net ads join raises an error and the server is not joined to the domain. What should be done to successfully join the domain?
What configuration directive of the Apache HTTPD server defines where log files are stored? (Specify ONE of the directives without any other options.)
What command creates a SSH key pair? (Specify ONLY the command without any path or parameters)
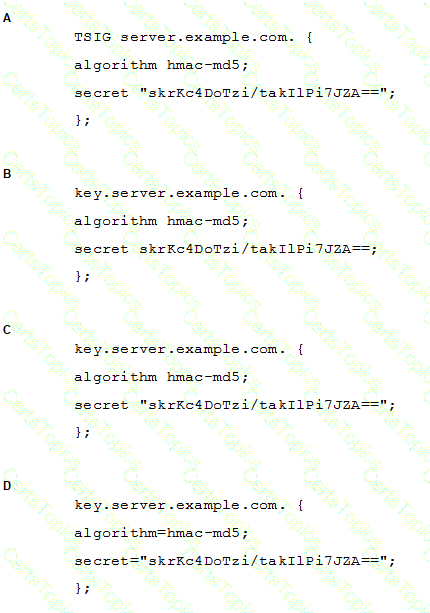
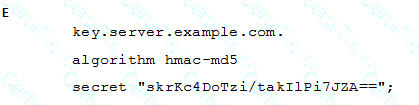
A BIND server should be upgraded to use TSIG. Which configuration parameters should be added if the server should use the algorithm hmac-md5 and the key skrKc4DoTzi/takIlPi7JZA==?
Which of the following Samba services handles the membership of a file server in an Active Directory domain?
On a Linux router, packet forwarding for IPv4 has been enabled. After a reboot, the machine no longer forwards IP packets from other hosts. The command:
echo 1 > /proc/sys/net/ipv4/ip_forward
temporarily resolves this issue.
Which one of the following options is the best way to ensure this setting is saved across system restarts?
What is the purpose of DANE?
Which keyword is used in the Squid configuration to define networks and times used to limit access to the service?
In order to prevent all anonymous FTP users from listing uploaded file names, what security precaution can be taken when creating an upload directory?
Which FTP names are recognized as anonymous users in vsftp when the option anonymous_enable is set to yes in the configuration files? (Choose two.)
Which Apache HTTPD directive enables HTTPS protocol support?
What is the name of the network security scanner project which, at the core, is a server with a set of network vulnerability tests?
If there is no access directive, what is the default setting for OpenLDAP?

The Samba configuration file contains the following lines:
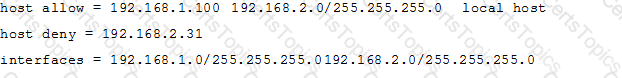
A workstation is on the wired network with an IP address of 192.168.1.177 but is unable to access the Samba server. A wireless laptop with an IP address 192.168.2.93 can access the Samba server. Additional trouble shooting shows that almost every machine on the wired network is unable to access the Samba server.
Which alternate host allow declaration will permit wired workstations to connect to the Samba server without denying access to anyone else?
Which of these tools, without any options, provides the most information when performing DNS queries?
Which option in named.conf specifies which host are permitted to ask for domain name information from the server?
Which global option in squid.conf sets the port number or numbers that Squid will use to listen for client requests?
To allow X connections to be forwarded from or through an SSH server, what configuration keyword must be set to yes in the sshd configuration file?
Which http_access directive for Squid allows users in the ACL named sales_net to only access the Internet at times specified in the time_acl named sales_time?
What is DNSSEC used for?
Which of the following actions are available in Sieve core filters? (Choose three.)
It has been discovered that the company mail server is configured as an open relay. Which of the following actions would help prevent the mail server from being used as an open relay while maintaining the possibility to receive company mails? (Choose two.)
Select the Samba option below that should be used if the main intention is to setup a guest printer service?
Which command is used to configure which file systems a NFS server makes available to clients?
When are Sieve filters usually applied to an email?
Which of the following types of IPv6 address assignments does DHCPv6 support? (Choose three.)
Which of the following options are valid in /etc/exports? (Choose two.)
Which Apache HTTPD configuration directive specifies the RSA private key that was used in the generation of the SSL certificate for the server?
Which doveadm sub-command displays a list of connections of Dovecot in the following format? (Specify ONLY the command without any parameters.)
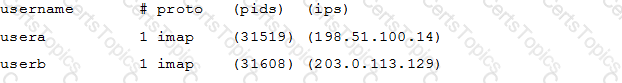
In a PAM configuration file, which of the following is true about the required control flag?
Which of the following commands can be used to connect and interact with remote TCP network services? (Choose two.)
What is the name of the root element of the LDAP tree holding the configuration of an OpenLDAP server that is using directory based configuration? (Specify ONLY the element’s name without any additional information.)
Which of the following DNS record types is used for reverse DNS queries?
When using mod_authz_core, which of the following strings can be used as an argument to Require in an Apache HTTPD configuration file to specify the authentication provider? (Choose three.)