Your company is acquiring a smaller company that uses the same private address range that your company currently uses in its North America division. You have a limited number of public IP addresses to use for the acquisition. You want to allow the new acquisition's users to connect to the existing services in North America.
Which two features would you enable on your SRX Series Firewall to accomplish this task? (Choose two.)
Which two statements about destination NAT are correct? (Choose two.)
You are asked to reduce security configuration complexity on your external facing firewalls. You notice that a previous administrator included hundreds of private subnet NAT rules covering various RFC1918 addresses. You want to replace all these rules with a single rule covering all RFC1918 addresses.
Which rule would you use in this scenario?
You are troubleshooting traffic traversing the SRX Series Firewall and require detailed information showing how the flow module is handling the traffic.
How would you accomplish this task?
You need to capture control plane traffic on a high-end SRX Series device.
How would you accomplish this task?
Click the Exhibit button.

Which type of policy is shown in the exhibit?
Click the Exhibit button.
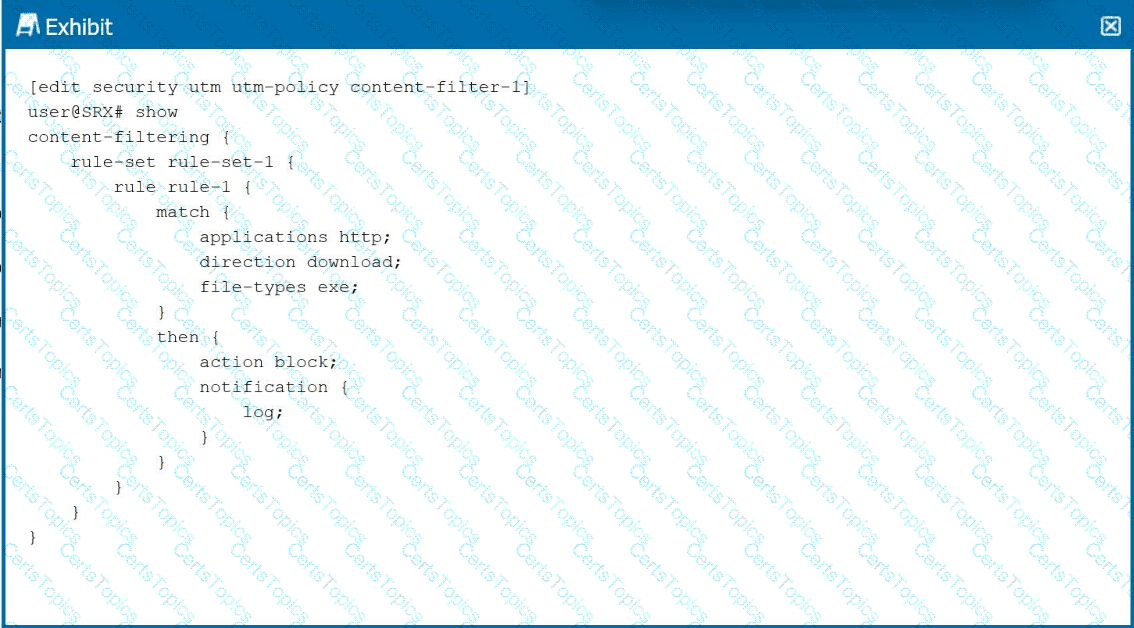
Which two statements are correct about the content filter shown in the exhibit? (Choose two.)
You want to enable NextGen Web Filtering in SRX Series devices.
In this scenario, which two actions will accomplish this task? (Choose two.)
Which two statements about SRX Series zones are correct? (Choose two.)
Which two statements about security zones are correct? (Choose two.)
Which two statements are true about the NextGen Web Filtering (NGWF) feature on an SRX Series device? (Choose two.)
You are troubleshooting first path traffic not passing through an SRX Series Firewall. You have determined that the traffic is ingressing and egressing the correct interfaces using a route lookup.
In this scenario, what is the next step in troubleshooting why the device may be dropping the traffic?
You are modifying the NAT rule order and you notice that a new NAT rule has been added to the bottom of the list.
In this situation, which command would you use to reorder NAT rules?
Which two criteria would be used for matching in security policies? (Choose two.)
You want to use Avira Antivirus.
Which two actions should you perform to satisfy this requirement? (Choose two.)
Which statement is correct about source NAT?
Which statement is correct about exception traffic?
What is the purpose of assigning logical interfaces to separate security zones in Junos OS?