Which of the following statements describes an engagement planning best practice?
Which of the following statements about internal audit's follow-up process is true?
The newly appointed chief audit executive (CAE) of a large multinational corporation, with seasoned internal audit departments located around the world, is reviewing responsibilities for engagement reports. According to IIA guidance, which of the following statements is true?
According to IIA guidance, which of the following would not be a consideration for the internal audit activity (IAA) when determining the need to follow-up on recommendations?
An organization's board would like to establish a formal risk management function and has asked the chief audit executive (CAE) to be involved in the process. According to IIA guidance, which of the following roles should the CAE not undertake?
After the team member who specialized in fraud investigations left the internal audit team, the chief audit executive decided to outsource fraud investigations to a third party service provider on an as needed basis. Which of the following is most likely to be a disadvantage of this outsourcing decision?
According to IIA guidance, which of the following statements best justifies a chief audit executive's request for external consultants to complement internal audit activity (IAA) resources?
During an assurance engagement, an internal auditor discovered that a sales manager approved numerous sales contracts for values exceeding his authorization limit. The auditor reported the finding to the audit supervisor, noting that the sales manager had additional new contracts under negotiation. According to IIA guidance, which of the following would be the most appropriate next step?
During an audit of the accounts receivable (AR) process, an internal auditor noted that reconciliations are still not performed regularly by the AR staff, a recommendation that was made following a previous audit. Monitoring by the financial reporting function has failed to detect the shortcoming. Both the financial reporting function and AR report to the controller, who is responsible for implementing action plans. Which of the following supports the internal auditor's decision to combine both observations into one reported finding?
Which of the following is a justifiable reason for omitting advance client notice when planning an audit engagement?
The chief risk officer (CRO) of a large manufacturing organization decided to facilitate a workshop for process managers and staff to identify opportunities for improving productivity and reducing defects. Which of the following is the most likely reason the CRO chose the workshop approach?
During a fraud interview, it was discovered that unquestioned authority enabled a vice president to steal funds from the organization. Which of the following best describes this condition?
According to IIA guidance, which of the following is least likely to be a key financial control in an organization's accounts payable process?
A newly promoted chief audit executive (CAE) is faced with a backlog of assurance engagement reports to review for approval. In an attempt to attach a priority for this review, the CAE scans the opinion statement on each report. According to IIA guidance, which of the following opinions would receive the lowest review priority?
1. Graded positive opinion.
2. Negative assurance opinion.
3. Limited assurance opinion.
4. Third-party opinion.
According to IIA guidance, organizations have the most influence on which element of fraud?
An internal auditor wants to determine whether employees are complying with the information security policy, which prohibits leaving sensitive information on employee desks overnight. The auditor checked a sample of 90 desks and found eight that contained sensitive information. How should this observation be reported, if the organization tolerates 4 percent noncompliance?
A chief audit executive (CAE) received a detailed internal report of senior management's internal control assessment. Which of the following subsequent actions by the CAE would provide the greatest assurance over management's assertions?
Which of the following best illustrates the primary focus of a risk-based approach to control self-assessment?
An internal auditor notes that employees continue to violate segregation-of-duty controls in several areas of the finance department, despite previous audit recommendations. Which of the following recommendations is the most appropriate to address this concern?
Which of the following is not a primary reason for outsourcing a portion of the internal audit activity?
According to the Standards, which of the following is leastimportant in determining the adequacy of an annual audit plan?
An internal auditor is conducting an assessment of the purchasing department. She has worked the full amount of hours budgeted for the engagement; however, the audit objectives are not yet complete. According to IIA guidance, which of the following are appropriate options available to the chief audit executive?
1. Allow the auditor to decide whether to extend the audit engagement.
2. Determine whether the work already completed is sufficient to conclude the engagement.
3. Provide the auditor feedback on areas of improvement for future engagements.
4. Provide the auditor with instructions and directions to complete the audit.
Due to price risk from the foreign currency purchase of aviation fuel, an airliner has purchased forward contracts to hedge against fluctuations in the exchange rate. When recalculating the exchange losses from individual purchases of jet fuel, which of the following details does the internal auditor need to validate?
1. The hedge documentation designating the hedge.
2. The spot exchange rate on the transaction date.
3. The terms of the forward contract.
4. The amount of fuel purchased.
An internal auditor submitted a report containing recommendations for management to enhance internal controls related to investments. To follow up, which of the following is the most appropriate action for the internal auditor to take?
A manufacturer is under contract to produce and deliver a number of aircraft to a major airline. As part of the contract, the manufacturer is also providing training to the airline's pilots. At the time of the audit, the delivery of the aircraft had fallen substantially behind schedule while the training had already been completed. If half of the aircraft under contract have been delivered, which of the following should the internal auditor expect to be accounted for in the general ledger?
A code of business conduct should include which of the following to increase its deterrent effect?
1. Appropriate descriptions of penalties for misconduct.
2. A notification that code of conduct violations may lead to criminal prosecution.
3. A description of violations that injure the interests of the employer.
4. A list of employees covered by the code of conduct.
According to IIA guidance, which of the following statements is true regarding the authority of the chief audit executive (CAE) to release previous audit reports to outside parties?
During an assurance engagement, an internal auditor noted that the time staff spent accessing customer information in large Excel spreadsheets could be reduced significantly through the use of macros. The auditor would like to train staff on how to use the macros. Which of the following is the most appropriate course of action for the internal auditor to take?
Which of the following is not a direct benefit of control self-assessment (CSA)?
Which of the following would not be a typical activity for the chief audit executive to perform following an audit engagement?
Which of the following options is the most cost-effective and efficient way for internal auditors to keep current with the latest developments in the internal audit profession?
The manager for an organization's accounts payable department resigned her post in that capacity. Three months later, she was recruited to the internal audit activity and has been working with the audit team for the last eight months. Which of the following assignments would the newly hired internal auditor be able to execute without any impairments to independence or objectivity?
According to IIA guidance, which of the following best describes internal auditors' responsibility regarding fraud?
A chief audit executive (CAE) is selecting an internal audit team to perform an audit engagement that requires a high level of knowledge in the areas of finance, investment portfolio management, and taxation. If neither the CAE nor the existing internal audit staff possess the required knowledge, which of the following actions should the CAE take?
According to IIA guidance, when preparing the charter for the internal audit activity, the chief audit executive (CAE), board, and senior management should agree on which of the following?
1. The standards to be used by the internal audit activity.
2. The internal audit activity's code of ethics.
3. The CAE's reporting line.
4. The internal audit activity's responsibilities.
According to IIA guidance, which of the following statements is true when an internal auditor performs consulting services that improve an organization's operations?
What is the purpose of a secondary control?
According to the COSO enterprise risk management framework, which of the following best describes the activity that helps ensure risk responses are carried out effectively?
Which of the following is considered a violation of The IIA's Code of Ethics?
Given the highly technical and legal nature of privacy issues, which of the following statements best describes the internal audit activity's responsibility with regard to assessing an organization's privacy framework?
Internal auditors must exercise due professional care by considering which of the following?
1. Cost of assurance in relation to potential benefits.
2. Adequacy and effectiveness of governance, risk management, and control processes.
3. Management's competency level in the area being evaluated.
4. Probability of significant errors, fraud, or noncompliance.
Which of the following would not be considered part of preliminary survey of an engagement area?
Which of the following actions would be characterized as a preventive control to safeguard inventory from the risk of theft?
1. Locking doors and physically securing inventory items.
2. Independently observing the receipt of materials.
3. Conducting monthly inventory counts.
4. Requiring the use of employee ID badges at all times.
Management is developing and implementing a risk and control framework for use throughout the organization. Which of the following elements should be included in the organization's control framework?
1. Appropriate levels of authority and responsibility.
2. Supervision of staff and appropriate review of work.
3. The seniority of management in the organization.
4. The ability to trace each transaction to an accountable and responsible individual.
A fraud investigation was completed by management, and a proven fraud was communicated to relevant authorities. According to MA guidance, which of the following roles would be most appropriate for the internal audit activity to undertake after the investigation?
An organization is beginning to implement an enterprise risk management program. One of the first steps is to develop a common risk language. Which of the following statements about a common risk language is true?
In the area of business acumen, which of the following competencies would be the sole responsibility of an internal audit staff member?
According to The MA Code of Ethics, which of the following is one of the rules of conduct for objectivity?
Which of the following controls could an internal auditor reasonably conclude is effective by observing the physical controls of a large server room?
Which of the following factors should be considered when determining the appropriate combination of manual techniques and computer-assisted audit techniques (CAATs) to be used during an audit?
1. Acceptance of CAATs findings by entity management.
2. Computer knowledge and expertise of the auditor.
3. Time constraints.
4. Level of audit risk.
Which of the following statements accurately describes an internal auditor's responsibility with regard to due professional care?
An internal audit charter, approved by the board, restricts the internal audit activity to providing assurance only on the reliability of financial information and the effectiveness of internal accounting controls. Which of the following statements is true regarding the extent to which the external auditor may rely on the internal audit activity's work?
As a matter of policy, the chief audit executive routinely rotates internal audit staff assignments and periodically interviews the staff to discuss the potential for conflicts of interest. These actions help fulfill which of the following internal audit mandates?
An organization has implemented a software system that requires a supervisor to approve transactions that would cause treasury dealers to exceed their authorized limit. This is an example of which of the following types of controls?
Which of the following actions should the audit committee take to promote organizational independence for the internal audit activity?
Which of the following would be the most important consideration by the internal audit activity when selecting employees to perform an internal quality assessment?
Which of the following types of social responsibilities is voluntary and guided purely by the organization's desire to make social contributions?
An auditor in charge was reviewing the workpapers submitted by a newly hired internal auditor. She noted that the new auditor's analytical work did not include any rating or quantification of the risk assessment results, and she returned the workpapers for correction. Which section of the workpapers will the new auditor need to modify?
According to IIA guidance, which of the following must internal auditors consider to conform with the requirements for due professional care during a consulting engagement?
1. The cost of the engagement, as it pertains to audit time and expenses in relation to the potential benefits.
2. The needs and expectation of clients, including the nature, timing, and communication of engagement results.
3. The application of technology-based audit and other data analysis techniques, where appropriate.
4. The relative complexity and extent of work needed to achieve the engagement's objectives.
What is the additional advantage of facilitated workshops, in comparison with structured interviews, used when testing the effectiveness of entity-level controls?
An organization decided to install a motion detection system in its warehouse to protect against after-hours theft. According to the COSO enterprise risk management framework, which of the following best describes this risk management strategy?
Which of the following is the best approach to overcome entry barriers into a new business?
A large hospital has an existing contract with a vendor in another country to provide software support and maintenance of the hospital's patient records information system. From the hospital management's perspective, which of the following controls would be most effective to address privacy risks related to this outsourcing arrangement^
Which of the following are typical audit considerations for a review of authentication?
1. Authentication policies and evaluation of controls transactions.
2. Management of passwords, independent reconciliation, and audit trail.
3. Control self-assessment tools used by management.
4. Independent verification of data integrity and accuracy.
Which of the following statements about market signaling is correct?
1. The organization releases information about a new product generation.
2. The organization limits a challenger's access to the best source of raw materials or labor.
3. The organization announces that it is fighting a new process technology.
4. The organization makes exclusive arrangements with the channels.
Which of the following is a typical example of structured data?
According to IIA guidance, which of the following steps are most important for an internal auditor to perform when evaluating an organization's social and environmental impact on the local community?
Which of the following options correctly defines a transmission control protocol/Internet protocol (TCP/IP)?
Which of the following best describes an objective for an audit of an environmental management system?
Which of the following is the most appropriate test to assess the privacy risks associated with an organization's workstations?
An organization is considering mirroring the customer data for one regional center at another center. A disadvantage of such an arrangement would be:
According to MA guidance on IT. which of the following would be considered a primary control for a spreadsheet to help ensure accurate financial reporting?
A department purchased one copy of a software program for internal use. The manager of the department installed the program on an office computer and then made two complete copies of the original software.
Copy 1 was solely for backup purposes.
Copy 2 was for use by another member of the department.
In terms of software licenses and copyright law, which of the following is correct?
The economic order quantity can be calculated using the following formula:
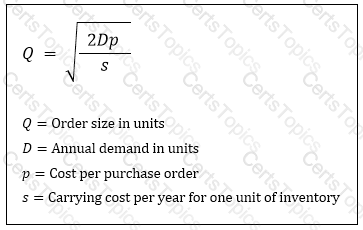
Which of the following describes how the optimal order size will change if the annual demand increases by 36 percent?
The board has requested that the internal audit activity be involved in all phases of the organization's outsourcing of its network management. During which of the following stages is the internal auditor most likely to verify that the organization's right-to-audit clause is drafted effectively?
Which of the following statements is true regarding a bring-your-own-device (BYOD) environment?
Under a value-added taxing system:
Listening effectiveness is best increased by:
Maintenance cost at a hospital was observed to increase as activity level increased. The following data was gathered:
Activity Level -
Maintenance Cost
Month
Patient Days
Incurred
January
5,600
$7,900
February
7,100
$8,500
March
5,000
$7,400
April
6,500
$8,200
May
7,300
$9,100
June
8,000
$9,800
If the cost of maintenance is expressed in an equation, what is the independent variable for this data?
Which of the following describes a typical desktop workstation used by most employees in their daily work?
Which of the following local area network physical layouts is subject to the greatest risk of failure if one device fails?
Which of the following are likely indicators of ineffective change management?
1. IT management is unable to predict how a change will impact interdependent systems or business processes.
2. There have been significant increases in trouble calls or in support hours logged by programmers.
3. There is a lack of turnover in the systems support and business analyst development groups.
4. Emergency changes that bypass the normal control process frequently are deemed necessary.
The economic order quantity for inventory is higher for an organization that has:
According to the Standards, the internal audit activity must evaluate risk exposures relating to which of the following when examining an organization's risk management process?
1. Organizational governance.
2. Organizational operations.
3. Organizational information systems.
4. Organizational structure.
Which of the following phases of a business cycle are marked by an underuse of resources?
1. The trough.
2. The peak.
3. The recovery.
4. The recession.
Which of the following control features consists of a set of authorization codes that distinguishes among actions such as reading, adding, and deleting records?
Which of the following is true regarding an organization's relationship with external stakeholders?
The main reason to establish internal controls in an organization is to:
Which of the following is an example of a smart device security control intended to prevent unauthorized users from gaining access to a device's data or applications?
According to IIA guidance on IT auditing, which of the following would not be an area examined by the internal audit activity?