Which two (2) columns are valid for searches in the My Offenses and All Offenses tabs in QRadar?
What is the default number of notifications that the System Notification dashboard can display?
A task is set up to identify events that were missed by the Custom Rule Engine. Which two (2) types of events does an analyst look for?
What are the behavioral rule test parameter options?
Which parameter is calculated based on the relevance, severity, and credibility of an offense?
AQRadar analyst can check the rule coverage of MITRE ATT&CK tactics and techniques by using Use Case Manager.
In the Use Case Manager app, how can a QRadar analyst check the offenses triggered and mapped to MITRE ATT&CK framework?
What type of rules will test events or flows for volume changes that occur in regular patterns to detect outliers?
In QRadar. what do event rules test against?
Events can be exported from the QRadar Log Activity tab in which file formats?
In QRadar. common rules test against what?
Which two (2) statements regarding indexed custom event properties are true?
How can an analyst search for all events that include the keyword "access"?
Which two (2) values are valid for the Offense Type field when a search is performed in the My Offenses or All Offenses tabs?
Several systems were initially reviewed as active offenses, but further analysis revealed that the traffic generated by these source systems is legitimate and should not contribute to offenses.
How can the activity be fine-tuned when multiple source systems are found to be generating the same event and targeting several systems?
Which property types can be used to reduce the overall data volume searched and shorten search time to address searches taking longer than expected?
An analyst must create a reference set collection containing the IPv6 addresses of command-and-control servers in an IBM X-Force Exchange collection in order to write a rule to detect any enterprise traffic with those malicious IP addresses.
What value type should the analyst select for the reference set?
How long will an AQL statement remain in execution if a time criteria is not specified, such as start, end, or last?
On the Reports tab in QRadar. what does the message "Queued (position in the queue)" indicate when generating a report?
To verify whether the login ID that was used to log in to QRadar is assigned to a user, create a list with the LoginlD parameter.
This example refers to what kind of reference data collections?
What happens when you select "False Positive" from the right-click menu in the Log Activity tab?
A QRadar analyst wants to limit the time period for which an AOL query is evaluated. Which functions and clauses could be used for this?
Which of these statements regarding the deletion of a generated content report is true?
Which two high level Event Categories are used by QRadar? (Choose two.)
What are two (2) Y-axis types that are available in the scatter chart type in the Pulse app?
A Security Analyst has noticed that an offense has been marked inactive.
How long had the offense been open since it had last been updated with new events or flows?
Which two (2) of these custom property expression types are supported in QRadar?
Which two (2) types of data can be displayed by default in the Application Overview dashboard?
a selection of events for further investigation to somebody who does not have access to the QRadar system.
Which of these approaches provides an accurate copy of the required data in a readable format?
How do events appear in QRadar if there was an error in the JSON parser for a new log source to which a custom log source extension was created?
Which two (2) tasks are uses of the QRadar network hierarchy?
What feature in QRadar uses existing asset profile data so administrators can define unknown server types and assign them to a server definition in building blocks and in the network hierarchy?
What Is the result of the following AQL statement?
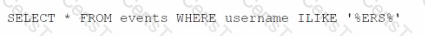
How does a Device Support Module (DSM) function?
From the Offense Summary window, how is the list of rules that contributed to a chained offense identified?
Which browser is officially supported for QRadar?
An analyst runs a search with correct AQL. but no errors or results are shown.
What is one reason this could occur?
How can an analyst improve the speed of searches in QRadar?
An analyst wants to share a dashboard in the Pulse app with colleagues.
The analyst exports the dashboard by using which format?
What right-click menu option can an analyst use to find information about an IP or URL?
A QRadar analyst would like to search for events that have fully matched rules which triggered offenses.
What parameter and value should the analyst add as filter in the event search?
Which two (2) AQL functions are used for calculations and formatting?