You work as a Network Administrator for Infosec Inc. The company has a Windows 2003-based server. You have installed McAfee antivirus as well as anti-spyware software on the server. One day, you come to know that not only have the security applications running on the server (including software firewalls, anti-virus, and anti-spyware) been disabled, but the anti-virus and anti-spyware definitions have also been deleted. You suspect that this is due to malware infection. Which of the following types of malware is the most likely cause of the issue?
Which of the following are the examples of administrative controls?
Each correct answer represents a complete solution. Choose all that apply.
You are an Incident manager in Orangesect.Inc. You have been tasked to set up a new extension of your enterprise. The networking, to be done in the new extension, requires different types of cables and an appropriate policy that will be decided by you. Which of the following stages in the Incident handling process involves your decision making?
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company has recently provided fifty laptops to its sales team members. You are required to configure an 802.11 wireless network for the laptops. The sales team members must be able to use their data placed at a server in a cabled network. The planned network should be able to handle the threat of unauthorized access and data interception by an unauthorized user. You are also required to prevent the sales team members from communicating directly to one another.
Which of the following actions will you perform to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools is based on Linux and used to carry out the Penetration Testing?
John is a merchant. He has set up a LAN in his office. Some important files are deleted as a result of virus attack. John wants to ensure that it does not happen again. What will he use to protect his data from virus?
Which of the following provides the best protection against a man-in-the-middle attack?
Which of the following password authentication schemes enables a user with a domain account to log on to a network once, using a password or smart card, and to gain access to multiple computers in the domain without being prompted to log in again?
You are the program manager for your organization. You have proposed a program that will cost $750,000 and will last for four years. Management is concerned with the cost of the program in relation to the return your program will bring. If the rate of return is six percent what is the minimum value your project should return in four years based on the investment of the program?
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
Which of the following protocols does IPsec use to perform various security functions in the network?
Each correct answer represents a complete solution. Choose all that apply.
A user has opened a Web site that automatically starts downloading malicious code onto his computer. What should he do to prevent this?
Each correct answer represents a complete solution. Choose two.
Fill in the blank with the appropriate tool name.
________ is a wireless network cracking tool that exploits the vulnerabilities in the RC4 Algorithm, which comprises the WEP security parameters.
Which of the following tools can be used for stress testing of a Web server?
Each correct answer represents a complete solution. Choose two.
Which of the following is a complete indexed set of records of the procurement process incorporated into the administrative closure process?
Which interface does an IPS sensor use to communicate with a security appliance for management purposes?
You are advising a school district on disaster recovery plans. In case a disaster affects the main IT centers for the district they will need to be able to work from an alternate location. However, budget is an issue. Which of the following is most appropriate for this client?
Which of the following is used to describe the type of FTP access in which a user does not have permissions to list the contents of directories, but can access the contents if he knows the path and file name?
Which of the following statements about Encapsulating Security Payload (ESP) is true?
Victor wants to send an encrypted message to his friend. He is using certain steganography technique to accomplish this task. He takes a cover object and changes it accordingly to hide information. This secret information is recovered only when the algorithm compares the changed cover with the original cover. Which of the following Steganography methods is Victor using to accomplish the task?
Which of the following viruses is designed to prevent antivirus researchers from examining its code by using various methods that make tracing and disassembling difficult?
IDS systems can be classified in many different ways. Which of the following is not a way that IDS systems are commonly classified?
Which of the following are examples of administrative controls that involve all levels of employees within an organization and determine which users have access to what resources and information?
Each correct answer represents a complete solution. Choose three.
Which of the following tools can be used for steganography?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the process of rewriting source and destination addresses of IP packets as they pass through a router or firewall?
Which of the following tools can be used to automate the MITM attack?
Which of the following statements are true about worms?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following Acts enacted in United States allows the FBI to issue National Security Letters (NSLs) to Internet service providers (ISPs) ordering them to disclose records about their customers?
Which of the following statements are true about TCP/IP model?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. You are working as a root user on the Linux operating system. Your company is facing an IP spoofing attack. Which of the following tools will you use to get an alert saying that an upcoming IP packet is being spoofed?
Which of the following is used to translate domain names into the numerical (binary) identifiers associated with networking equipment for the purpose of locating and addressing these devices worldwide?
Which of the following are the countermeasures against a man-in-the-middle attack?
Each correct answer represents a complete solution. Choose all that apply.
Part of your change management plan details what should happen in the change control system for your project. Theresa, a junior project manager, asks what the configuration management activities are for scope changes. You tell her that all of the following are valid configuration management activities except for which one?
A sequence number is a 32-bit number ranging from 1 to 4,294,967,295. When data is sent over the network, it is broken into fragments (packets) at the source and reassembled at the destination system. Each packet contains a sequence number that is used by the destination system to reassemble the data packets in the correct order. The Initial Sequence Number of your computer is 24171311 at login time. You connect your computer to a computer having the IP address 210.213.23.21. This whole process takes three seconds. What will the value of the Initial Sequence Number be at this moment?
In which of the following techniques does an attacker change the address of the phishing site in such a manner that it can bypass filters or other application defenses that have been put in place to block specific IP addresses?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of He receives the following e-mail:
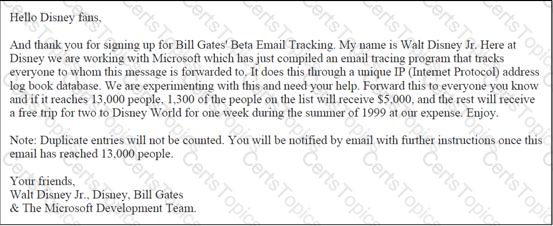
The e-mail that John has received is an example of __________.
Complete the following sentence: Quality control is a(n)_______________ process while quality assurance is a(n)________________ process.
The Incident handling process implemented in an enterprise is responsible to deal with all the incidents regarding the enterprise. Which of the following procedures will be involved by the preparation phase of the Incident handling process?
You work as a project manager for an IT project. You are analyzing activity sequences, durations, resource requirements, and schedule constraints to create the project schedule. In which of the following Knowledge Areas are you working on?
You work as an Exchange Administrator for McRobert Inc. You are configuring a new Exchange 2000 Server computer and two storage groups, group A and group B, on your network. You have to configure the physical disks on the Exchange 2000 Server computer to provide better performance and availability. Which configuration will you use to achieve this?
How can you calculate the Annualized Loss Expectancy (ALE) that may occur due to a threat?
Rick is a project manager of a construction project. He is aggregating the estimated costs of individual activities or work packages to establish a cost baseline. In which of the following Project Management Knowledge Areas is he working on?
Mark works as a Network Administrator for BlueWell Inc. While surfing the Internet, he enters a URL in the Web browser. A Web page appears after entering the URL. Which of the following protocols can be used to resolve into the correct IP address?
You work as a Network Administrator for Net World Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. A Public Key Infrastructure (PKI) is installed on a server in the domain. You are planning to go on vacation for two weeks. Your team has three assistant administrators. You are required to accomplish the following tasks:
• Delegate the authority to the assistant administrators to issue, approve, and revoke certificates.
• The solution must involve least administrative burden.
Which of the following steps will you take to accomplish the tasks?
You have inserted a Trojan on your friend's computer and you want to put it in the startup so that whenever the computer reboots the Trojan will start to run on the startup. Which of the following registry entries will you edit to accomplish the task?
You work as a technician for Tech Perfect Inc. A user named Rick calls you. He wants to configure a wireless network for his small office. He wants to adopt a wireless technology that supports high data transfer speed. Which of the following technologies will you suggest?
You are the project manager of a large project that will span several time zones. You'll be utilizing project team members from across several departments. Project team members won't be working on the project full-time and will join and leave the project based on assignments in the project schedule.
What project management plan can you create to help you manage when project times will be brought onto and released from the project team?
Which of the following RAID standards distributes data across multiple disks in a way that gives improved speed at any given instant?
Maria works as a Network Security Officer for Gentech Inc. She wants to encrypt her network traffic. The specific requirement for the encryption algorithm is that it must be a symmetric key block cipher.
Which of the following techniques will she use to fulfill this requirement?
John works as a Network Administrator for We-are-secure Inc. The We-are-secure server is based on Windows Server 2003. One day, while analyzing the network security, he receives an error message that Kernel32.exe is encountering a problem. Which of the following steps should John take as a countermeasure to this situation?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following programs can be used to detect stealth port scans performed by a malicious hacker?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following types of attacks cannot be prevented by a firewall?
Each correct answer represents a complete solution. Choose all that apply.
You are responsible for the security computers in college labs. Since a number of students have significant computer skills, you wish to make security impossible to breach through normal operating system based means. Furthermore, you want to have the security require a password that must be entered before the operating system even loads. What will you do to accomplish the task?
Which of the following malware spread through the Internet and caused a large DoS attack in 1988?
Which method is used to configure several disk drives into a logical disk drive and provides faulttolerance, redundancy, lower latency, and higher bandwidth for read/write operations?
John is a malicious attacker. He illegally accesses the server of We-are-secure Inc. He then places a backdoor in the We-are-secure server and alters its log files. Which of the following steps of malicious hacking includes altering the server log files?
Dawn is the project manager of the HQQ Project and she believes the project work is done. She has prepared the final project report, which includes information on the financial performance, schedule performance, and project team performance in the project. All of the following documents are used to measure the completeness of the project scope except for which one?
Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
An executive in your company reports odd behavior on her PDA. After investigation you discover that a trusted device is actually copying data off the PDA. The executive tells you that the behavior started shortly after accepting an e-business card from an unknown person. What type of attack is this?
This type of virus infects programs that can execute and load into memory to perform predefined steps for infecting systems. It infects files with the extensions .EXE, .COM, .BIN, and .SYS. As it can replicate or destroy these types of files, the operating system becomes corrupted and needs reinstallation. This type of virus is known as __________.
Joseph works as a Network Administrator for WebTech Inc. He has to set up a centralized area on the network so that each employee can share resources and documents with one another. Which of the following will he configure to accomplish the task?
John works as a professional Ethical Hacker. He is assigned a project to test the security of He enters a single quote in the input field of the login page of the We-are- secure Web site and receives the following error message:
Microsoft OLE DB Provider for ODBC Drivers error '0x80040E14'
This error message shows that the We-are-secure Website is vulnerable to __________.
Which of the following documents is described in the statement below?
"It is developed along with all processes of the risk management. It contains the results of the qualitative risk analysis, quantitative risk analysis, and risk response planning."
You work as an Incident handler in Mariotrixt.Inc. You have followed the Incident handling process to handle the events and incidents. You identify Denial of Service attack (DOS) from a network linked to your internal enterprise network. Which of the following phases of the Incident handling process should you follow next to handle this incident?
Which of the following recovery plans includes specific strategies and actions to deal with specific variances to assumptions resulting in a particular security problem, emergency, or state of affairs?
You work as a Network Administrator for Net Perfect Inc. The company has a TCP/IP-based network environment. The network contains a Cisco Catalyst router to connect the internal network to the Internet. You want to secure your network from various attacks such as virus, spam, spyware, phishing, etc. You want to secure the whole network through a separate hardware device. Which of the following will you use?
Which of the following viruses replaces the boot sector data with its own malicious code?
The Project Scope Management knowledge area focuses on which of the following processes?
Each correct answer represents a complete solution. Choose all that apply.
You are the Administrator of a Windows 2000 based network for Info Tech Inc. You install and configure Certificate Authorities (CAs) on the network. You are currently configuring the public key group policy for the domain.
You configure the group policy to specify automatic enrollment and renewal for certificates. But when you attempt to test this configuration, you find that the enrollment is not working properly.
What is the most likely cause?
Which of the following authentication methods is used to enable a Web browser to provide credentials when making a request during an HTTP transaction?
You are concerned about attackers simply passing by your office, discovering your wireless network, and getting into your network via the wireless connection. Which of the following are NOT steps in securing your wireless connection?
Each correct answer represents a complete solution. Choose two.
What does noise in a power line indicate?
In Which of the following types of white box testing are the test cases designed based on data flow within the code?
Which type of repudiation states that the creator of the message denies ever creating the message even after creating it?
Which of the following is used to indicate that the project team has decided not to change the project management plan to deal with a risk or is unable to identify any other suitable response strategy?
Which of the following port numbers is used by the LDAP protocol when it is secured?
Which of the following tools can be used to perform polymorphic shell code attacks?
You work as a Network Administrator in a company. The NIDS is implemented on the network. You want to monitor network traffic. Which of the following modes will you configure on the network interface card to accomplish the task?
Which of the following is a cryptographic approach employed by many cryptographic algorithms and cryptosystems?
Your IDS discovers that an intruder has gained access to your system. You immediately stop that access, change passwords for administrative accounts, and secure your network. You discover an odd account (not administrative) that has permission to remotely access the network. What is this most likely?
SSH is a network protocol that allows data to be exchanged between two networks using a secure channel. Which of the following encryption algorithms can be used by the SSH protocol?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following colors is used for ultra secret information?
Joseph works as a Network Administrator for WebTech Inc. He has to set up a centralized area on the network so that each employee can share resources and documents with one another. Which of the following will he configure to accomplish the task?
Which of the following is an input of the close procurements process?
Which of the following is a type of encryption that uses a single key to encrypt and decrypt data?