Which two settings are automatically pushed from FortiSASE to FortiClient in a new FortiSASE deployment with default settings? (Choose two answers)
A company must provide access to a web server through FortiSASE secure private access for contractors. What is the recommended method to provide access? (Choose one answer)
A Fortinet customer is considering integrating FortiManager with FortiSASE. What are two prerequisites they should consider? (Choose two answers)
A FortiSASE administrator is receiving reports that some users have travelled overseas and cannot establish their agent-based VPN tunnels, although they can authenticate with their SSO credentials to access O365 and SFDC directly. The administrator reviewed the firewall policies and ZTNA tags of some users and could not find anything unusual. Which action can the administrator take to resolve this problem? (Choose one answer)
Which policy type is used to control traffic between the FortiClient endpoint to FortiSASE for secure internet access?
Refer to the exhibit.
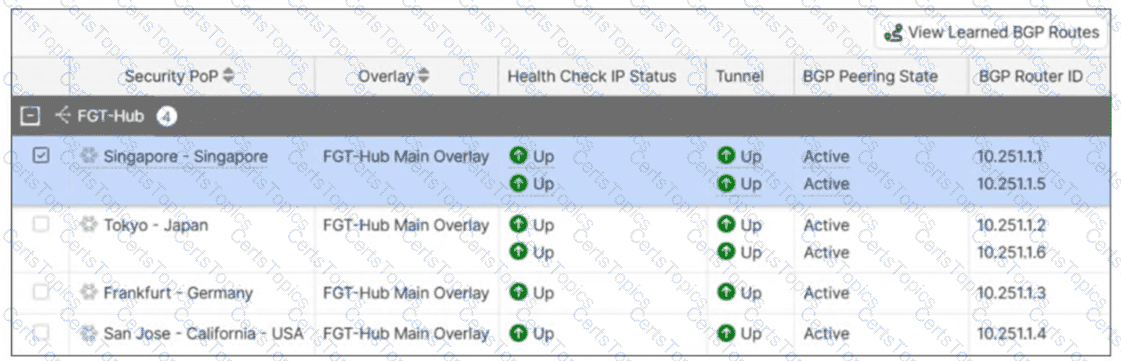
An SPA service connection is experiencing connectivity problems. Which configuration setting should the administrator verify and correct first? (Choose one answer)
Which service is included in a secure access service edge (SASE) solution, but not in a security service edge (SSE) solution? (Choose one answer)
You are designing a new network, and the cybersecurity policy mandates that all remote users working from home must always be connected and protected. Which FortiSASE component facilitates this always-on security measure? (Choose one answer)
What are the two key features and benefits of Fortinet SOCaaS when integrated with FortiSASE? (Choose two answers)
An administrator must restrict endpoints from certain countries from connecting to FortiSASE. Which configuration can achieve this? (Choose one answer)
Which FortiSASE feature ensures least-privileged user access to all applications?
What happens to the logs on FortiSASE that are older than the configured log retention period? (Choose one answer)
To complete their day-to-day operations, remote users require access to a TCP-based application that is hosted on a private web server. Which FortiSASE deployment use case provides the most efficient and secure method for meeting the remote users' requirements?
What action must a FortiSASE customer take to restrict organization SaaS access to only FortiSASE-connected users? (Choose one answer)
An organization needs to resolve internal hostnames using its internal rather than public DNS servers for remotely connected endpoints. Which two components must be configured on FortiSASE to achieve this? (Choose two.)
Which secure internet access (SIA) use case minimizes individual workstation or device setup, because you do not need to install FortiClient on endpoints or configure explicit web proxy settings on web browser-based end points?
Which authentication method overrides any other previously configured user authentication on FortiSASE?
When configuring the DLP rule in FortiSASE using Regex format, what would be the correct order for the configuration steps? (Place the four correct steps in order)

You have configured FortiSASE Secure Private Access (SPA) deployment. Which statement is true about traffic flows? (Choose two answers)
How does FortiSASE address the market trends of multicloud and Software-as-a-Service (SaaS) adoption, hybrid workforce, and zero trust? (Choose one answer)
A customer configured the On/off-net detection rule to disable FortiSASE VPN auto-connect when users are inside the corporate network. The rule is set to Connects with a known public IP using the company’s public IP address. However, when the users are on the corporate network, the FortiSASE VPN still auto-connects. The customer has confirmed that traffic is going to the internet with the correct IP address.
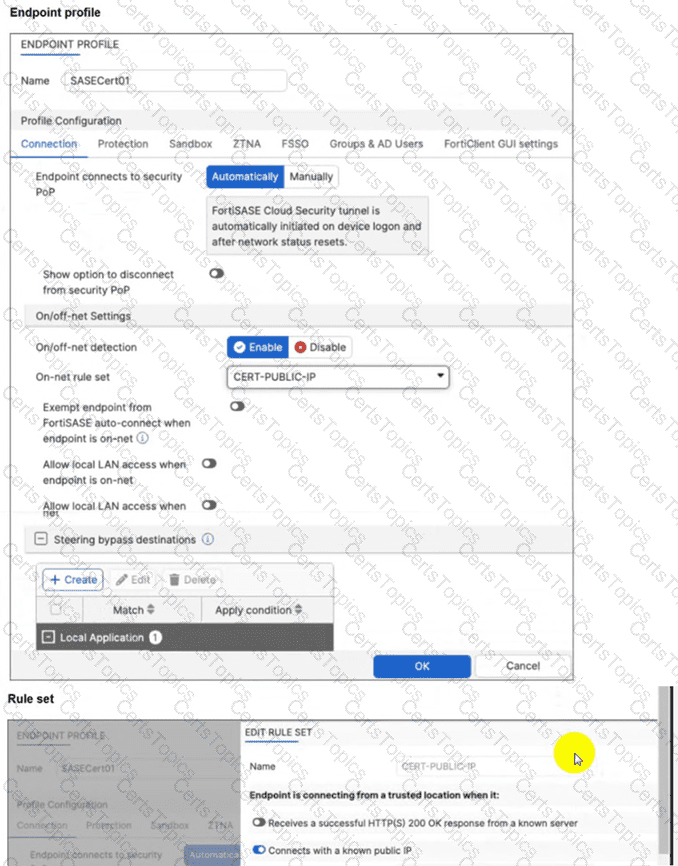
Which configuration is causing the issue? (Choose one answer)
Your FortiSASE customer has a small branch office in which ten users will be using their personal laptops and mobile devices to access the internet. Which deployment should they use to secure their internet access with minimal configuration? (Choose one answer)
Which two statements about FortiSASE Geofencing with regional compliance are true? (Choose two answers)
Refer to the exhibit.
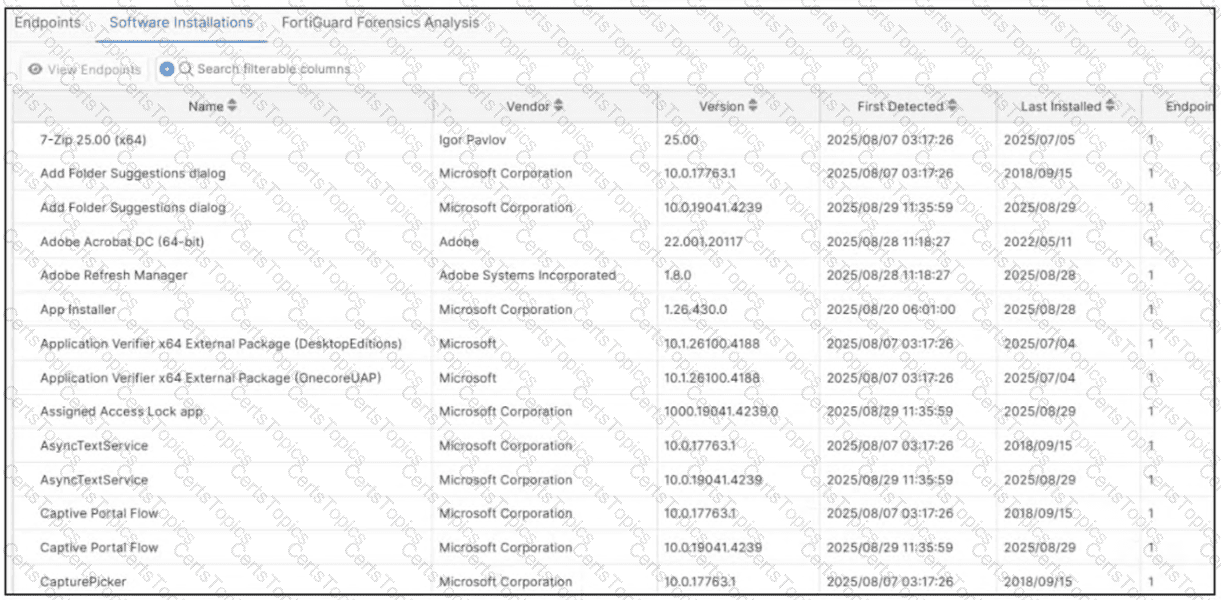
Which type of information or actions are available to a FortiSASE administrator from the following output? (Choose one answer)