Refer to the exhibit
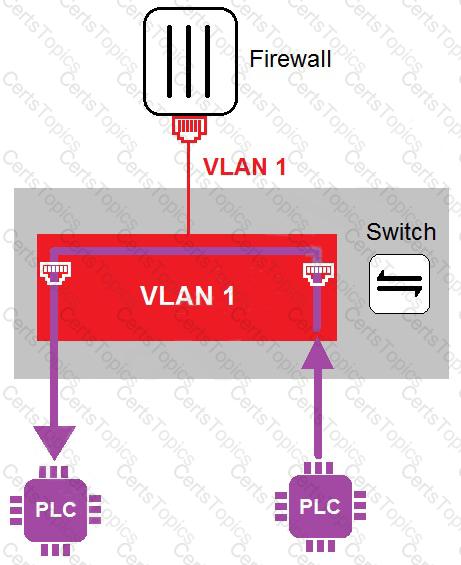
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
Refer to the exhibit and analyze the output.
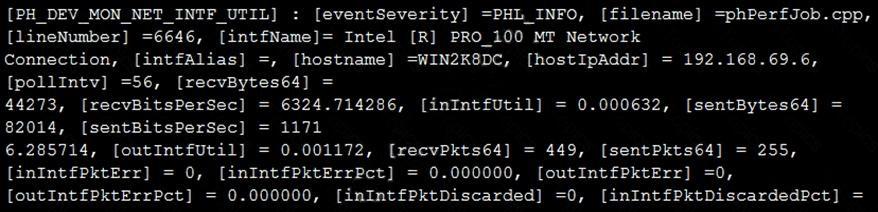
Which statement about the output is true?
What triggers Layer 2 polling of infrastructure devices connected in the network?
Refer to the exhibit.
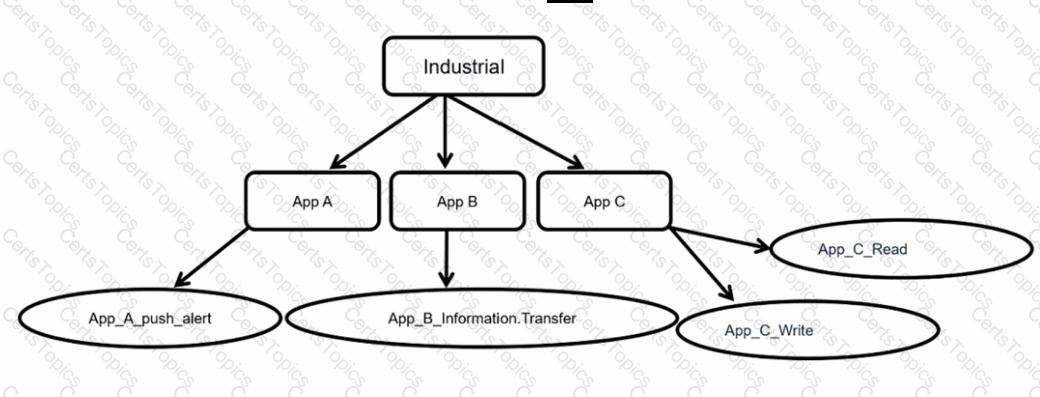
Which statement is true about application control inspection?
What is the primary objective of implementing SD-WAN in operational technology (OT) networks'?
Refer to the exhibit.
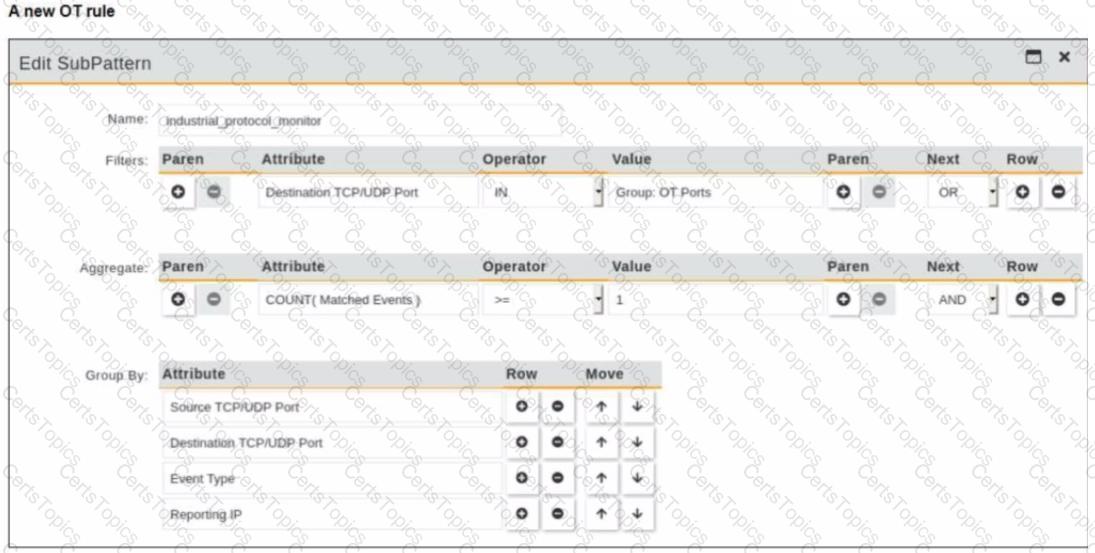
You are creating a new operational technology (OT) rule to monitor Modbus protocol traffic on FortiSIEM
Which action must you take to ensure that all Modbus messages on the network match the rule?
An OT network consists of multiple FortiGate devices. The edge FortiGate device is deployed as the secure gateway and is only allowing remote operators to access the ICS networks on site.
Management hires a third-party company to conduct health and safety on site. The third-party company must have outbound access to external resources.
As the OT network administrator, what is the best scenario to provide external access to the third-party company while continuing to secure the ICS networks?
in an operation technology (OT) network FortiAnalyzer is used to receive and process logs from responsible FortiGate devices
Which statement about why FortiAnalyzer is receiving and processing multiple tog messages from a given programmable logic controller (PLC) or remote terminal unit (RTU) is true'?
An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted from credentials during authentication.
What is a possible reason?
As an OT administrator, it is important to understand how industrial protocols work in an OT network.
Which communication method is used by the Modbus protocol?
The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
Refer to the exhibit.
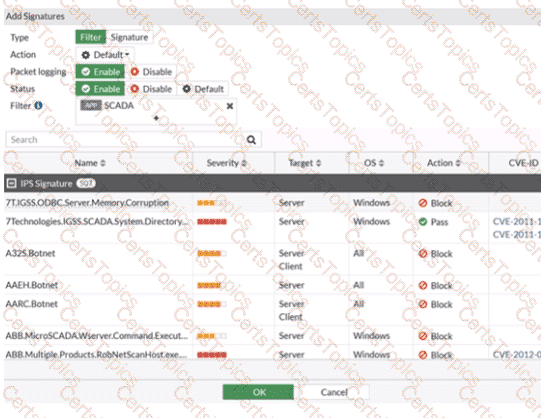
The IPS profile is added on all of the security policies on FortiGate.
For an OT network, which statement of the IPS profile is true?
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
An OT supervisor needs to protect their network by implementing security with an industrial signature database on the FortiGate device.
Which statement about the industrial signature database on FortiGate is true?
An OT administrator configured and ran a default application risk and control report in FortiAnalyzer to learn more about the key application crossing the network. However, the report output is empty despite the fact that some related real-time and historical logs are visible in the FortiAnalyzer.
What are two possible reasons why the report output was empty? (Choose two.)
With the limit of using one firewall device, the administrator enables multi-VDOM on FortiGate to provide independent multiple security domains to each ICS network. Which statement ensures security protection is in place for all ICS networks?
Which statement about the IEC 104 protocol is true?
An OT administrator is defining an incident notification policy using FortiSIEM and would like to configure the system with a notification policy. If an incident occurs, the administrator would like to be able to intervene and block an IP address or disable a user in Active Directory from FortiSIEM.
Which step must the administrator take to achieve this task?
In a wireless network integration, how does FortiNAC obtain connecting MAC address information?
Which two statements are true when you deploy FortiGate as an offline IDS? (Choose two.)