In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
An administrator is configuring FortiNAC to manage FortiGate VPN users. As part of the configuration, the administrator must configure a few FortiGate firewall policies.
What is the purpose of the FortiGate firewall policy that applies to unauthorized VPN clients?
In an isolation VLAN which three services does FortiNAC supply? (Choose three.)
What agent is required in order to detect an added USB drive?
Which group type can have members added directly from the FortiNAC Control Manager?
In which view would you find who made modifications to a Group?
Refer to the exhibit.
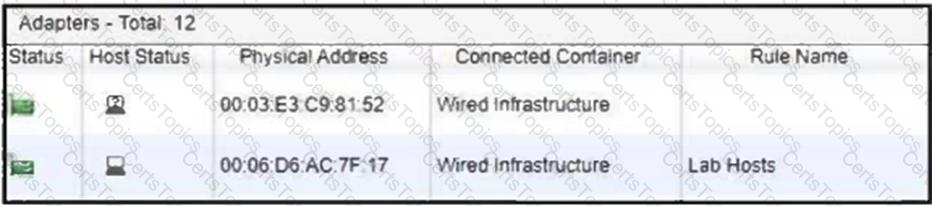
Considering the host status of the two hosts connected to the same wired port, what will happen if the port is a member of the Forced Registration port group?
View the command and output shown in the exhibit.
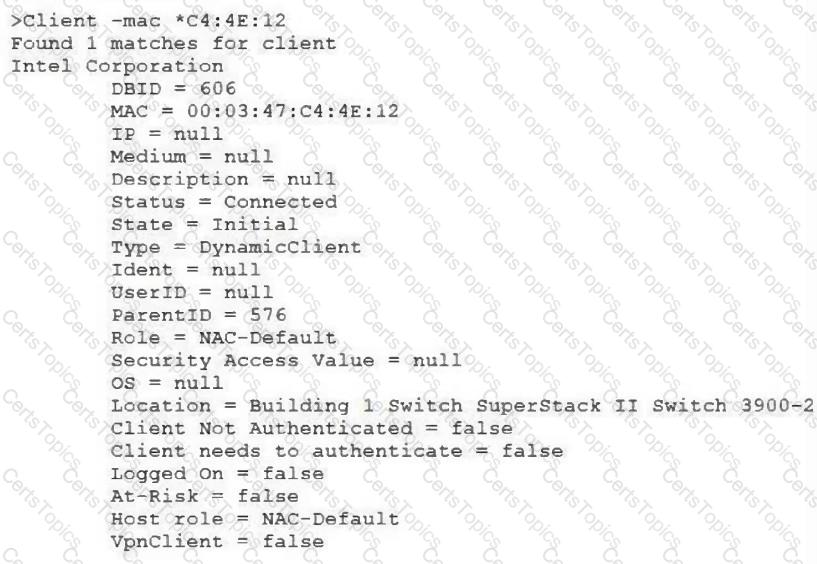
What is the current state of this host?
Which three circumstances trigger Layer 2 polling of infrastructure devices? (Choose three.)
Which system group will force at-risk hosts into the quarantine network, based on point of connection?
Which three of the following are components of a security rule? (Choose three.)
Which two things must be done to allow FortiNAC to process incoming syslog messages from an unknown vendor? (Choose two.)
Where should you configure MAC notification traps on a supported switch?
What capability do logical networks provide?