Refer to the exhibit which displays a list of IBE users on a FortiMail device.
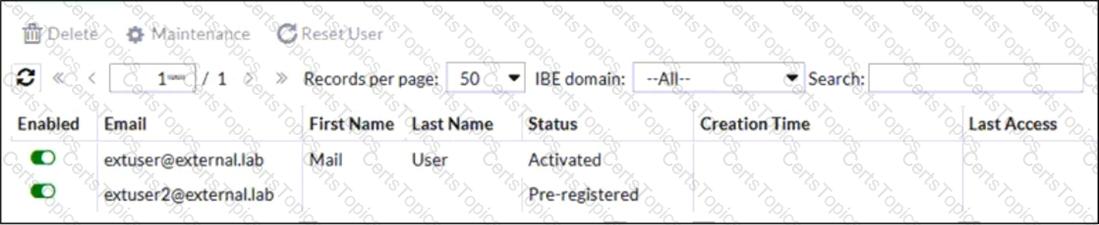
Which statement describes the pre-registered status of the IBE user extuser2@external.lab?
Refer to the exhibit which displays the domain configuration of a transparent mode FortiMail device.
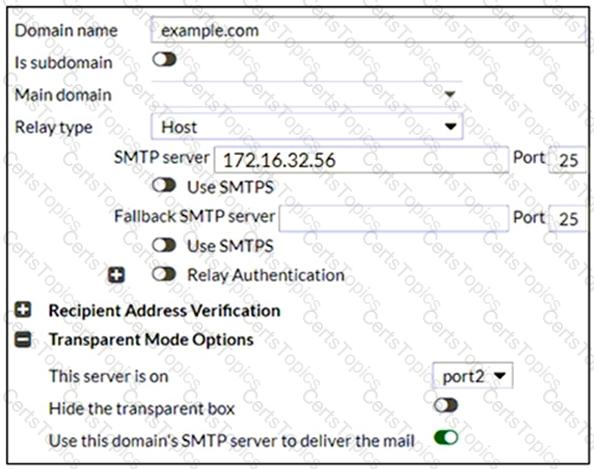
Based on the exhibit, which two sessions are considered incoming sessions? (Choose two.)
In which two places can the maximum email size be overridden on FortiMail? (Choose two.)
Which two FortiMail antispam techniques can you use to combat zero-day spam? (Choose two.)
Which two features are available when you enable HA centralized monitoring on FortiMail? (Choose two.)
Refer to the exhibit which shows a topology diagram of a FortiMail cluster deployment.
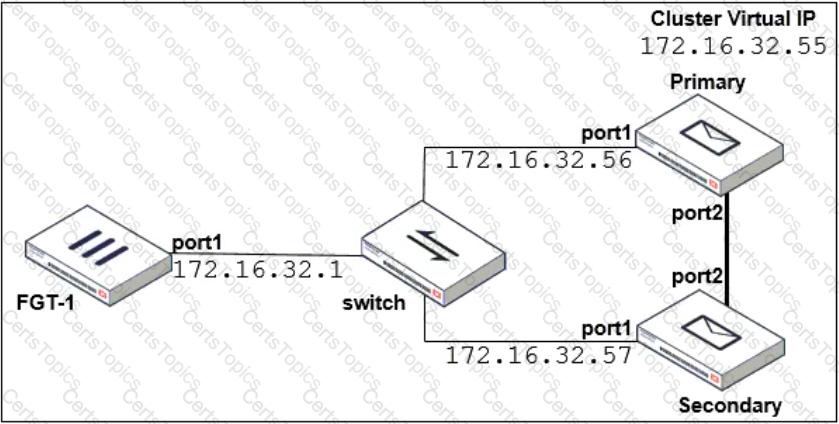
Which IP address must the DNS MX record for this organization resolve to?
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas.
Which FortiMail feature specific to server mode can be used to accomplish this?
Refer to the exhibit, which shows an inbound recipient policy.
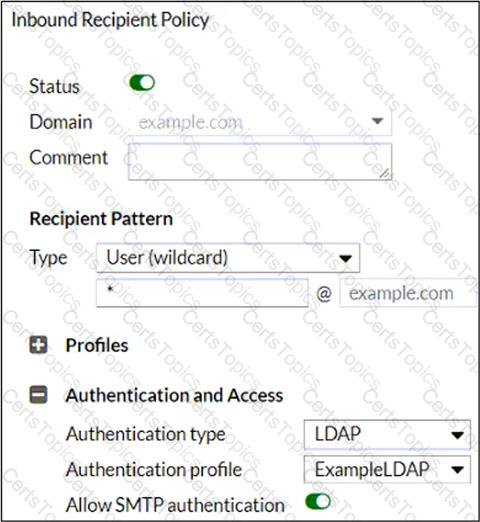
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
What are two disadvantages of configuring the dictionary and DLP scan rule aggressiveness too high? (Choose two.)