The IT team is wondering whether they will need to continue using MDM tools for future FortiClient upgrades.
What options are available for handling future FortiClient upgrades?
SD-WAN interacts with many other FortiGate features. Some of them are required to allow SD-WAN to steer the traffic.
Which three configuration elements must you configure before FortiGate can steer traffic according to SD-WAN rules? (Choose three.)
Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule? (Choose two answers)
A FortiGate device is in production. To optimize WAN link use and improve redundancy, you enable and configure SD-WAN.
What must you do as part of this configuration update process? (Choose one answer)
For a small site, an administrator plans to implement SD-WAN and ensure high network availability for business-critical applications while limiting the overall cost and the cost of pay-per-use backup connections.
Which action must the administrator take to accomplish this plan?
Refer to the exhibit.
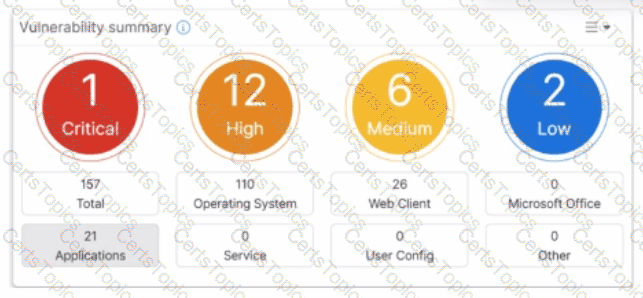
Which two statements about the Vulnerability summary dashboard in FortiSASE are correct? (Choose two.)
What is a key use case for FortiSASE Secure Internet Access (SIA) in an agentless deployment? (Choose one answer)
An existing Fortinet SD-WAN customer who has recently deployed FortiSASE wants to have a comprehensive view of, and combined reports for, both SD-WAN branches and remote users. How can the customer achieve this?
You have a FortiGate configuration with three user-defined SD-WAN zones and one or two members in each of these zones. One SD-WAN member is no longer used in health-check and SD-WAN rules. This member is the only member of its zone. You want to delete it.
What happens if you delete the SD-WAN member from the FortiGate GUI?
You want FortiGate to use SD-WAN rules to steer ping local-out traffic. Which two constraints should you consider? (Choose two.)