Refer to the exhibit.
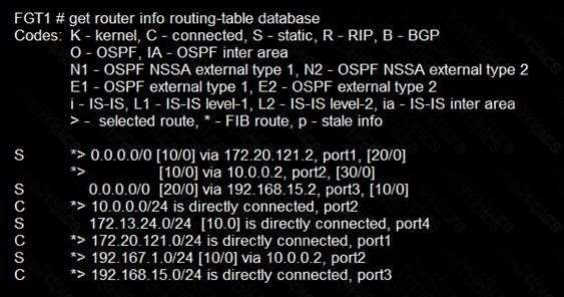
Given the routing database shown in the exhibit, which two statements are correct? (Choose two.)
113
What inspection mode does FortiGate use if it is configured as a policy-based next-generation firewall (NGFW)?
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
An administrator is running the following sniffer command:
Which three pieces of Information will be Included in me sniffer output? {Choose three.)
Which three criteria can a FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
51
Which of the following statements about central NAT are true? (Choose two.)
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
40
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
24
To complete the final step of a Security Fabric configuration, an administrator must authorize all the devices on
which device?
Refer to the exhibit.
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 status is up, but phase 2 fails to come up.
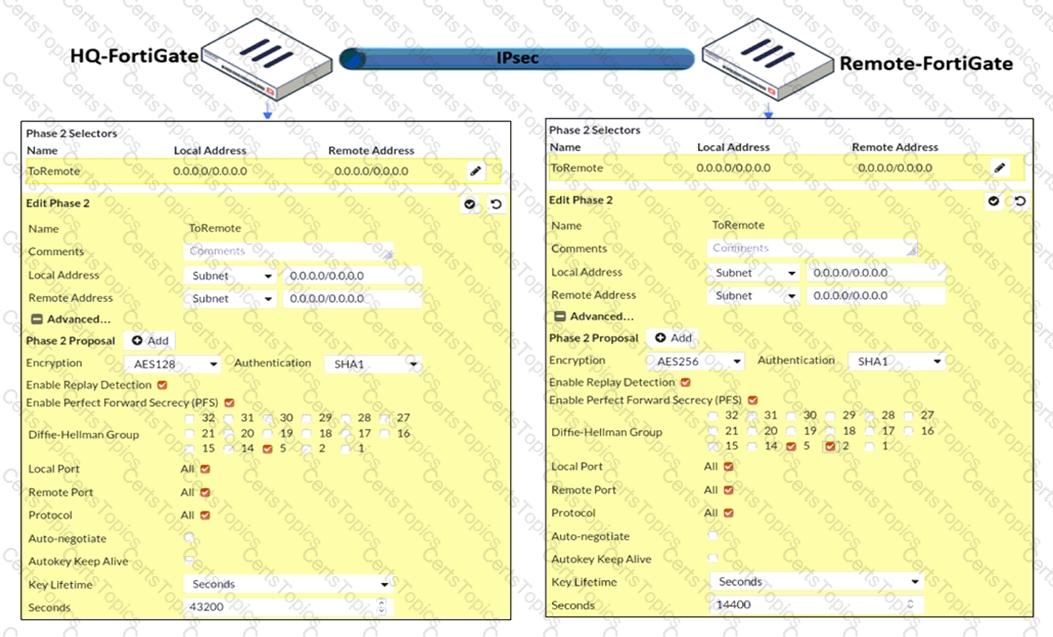
Based on the phase 2 configuration shown in the exhibit, which configuration change will bring phase 2 up?
55
In which two ways can RPF checking be disabled? (Choose two )
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
Refer to the exhibit.
The exhibit shows the output of a diagnose command.
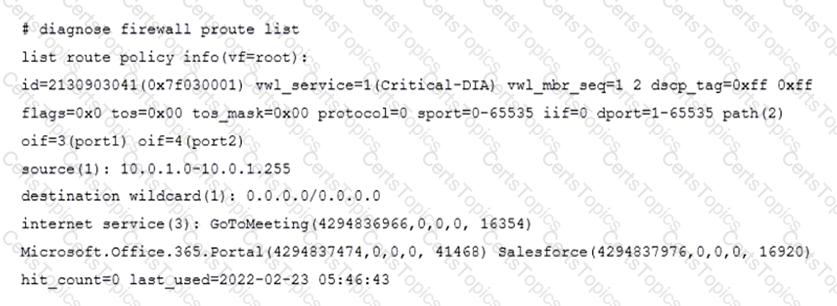
What does the output reveal about the policy route?
68
If the Services field is configured in a Virtual IP (VIP), which statement is true when central NAT is used?
Refer to exhibit.
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
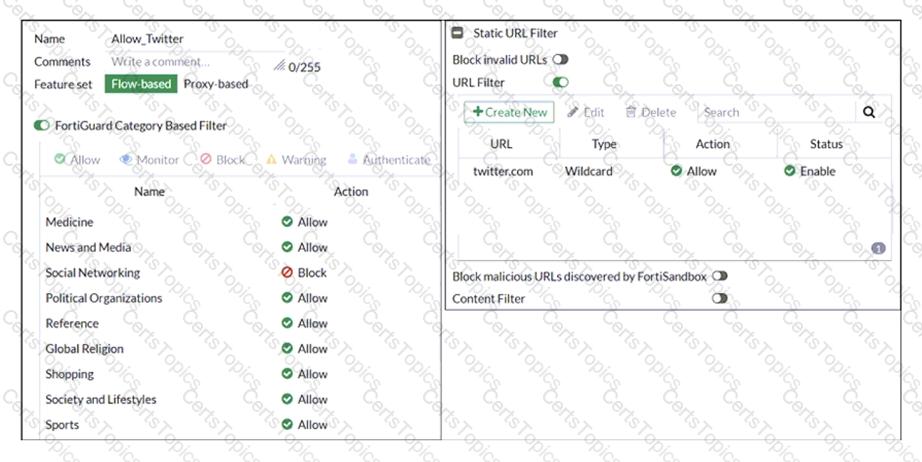
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
56
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
Refer to the exhibits.
The exhibits show the firewall policies and the objects used in the firewall policies.
The administrator is using the Policy Lookup feature and has entered the search criteria shown in the exhibit.
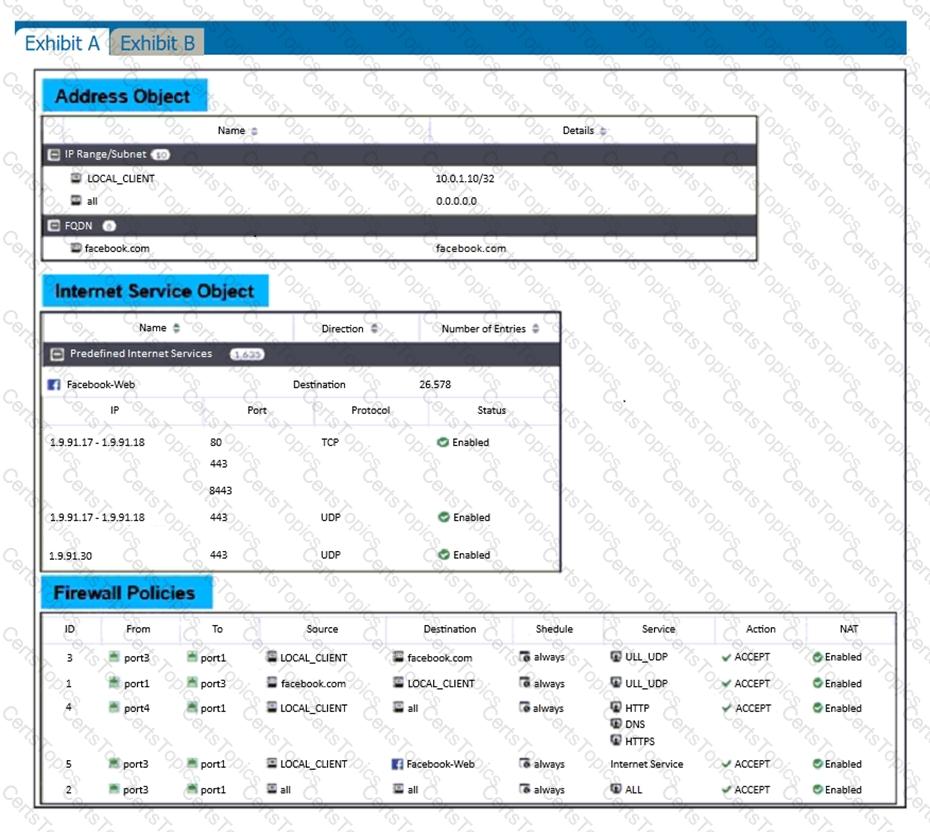
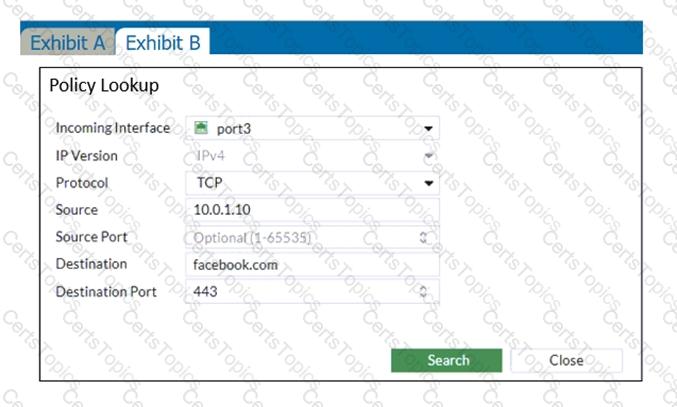
Which policy will be highlighted, based on the input criteria?
46
Which two types of traffic are managed only by the management VDOM? (Choose two.)
Refer to the exhibits.

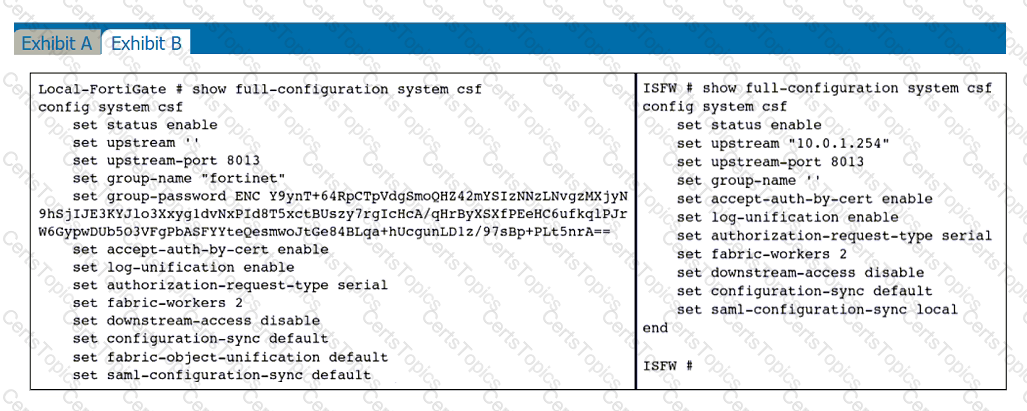
An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).
What must the administrator do to synchronize the address object?
58
Refer to the exhibit.
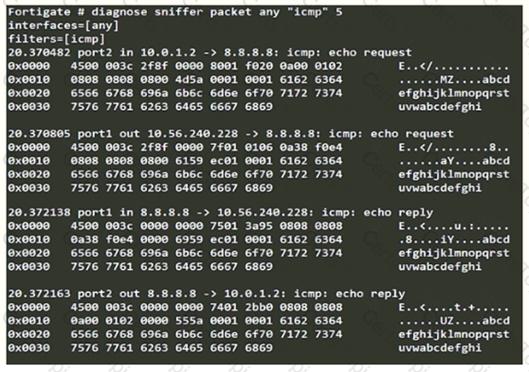
An administrator is running a sniffer command as shown in the exhibit.
Which three pieces of information are included in the sniffer output? (Choose three.)
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network, the firewall policy and VIP configuration on the FortiGate device, and the routing table on the ISP router.
When the administrator tries to access the web server public address (203.0.113.2) from the internet, the connection times out. At the same time, the administrator runs a sniffer on FortiGate to capture incoming web traffic to the server and does not see any output.
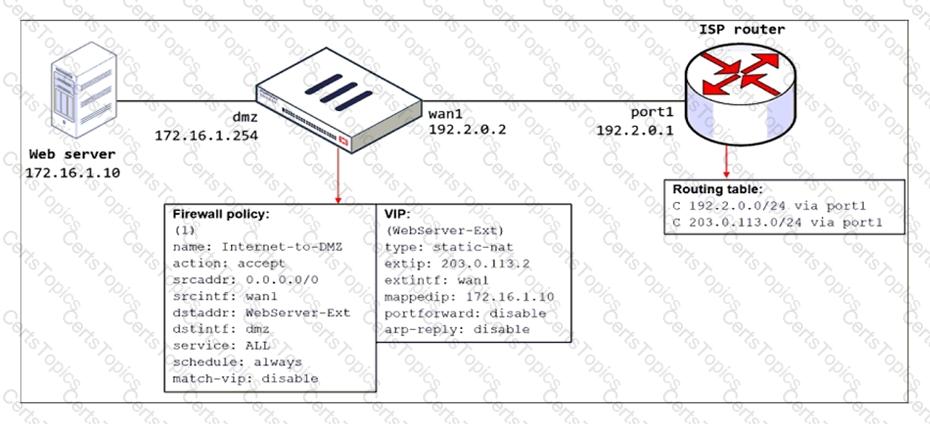
Based on the information shown in the exhibit, what configuration change must the administrator make to fix the connectivity issue?
What are two benefits of flow-based inspection compared to proxy-based inspection? (Choose two.)
Refer to the exhibit.
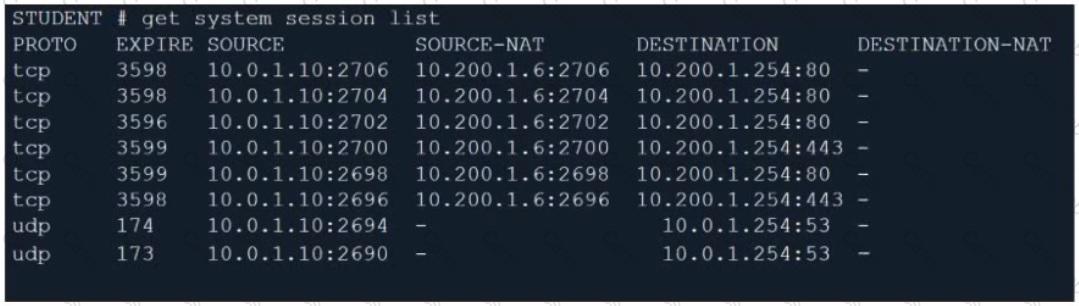
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
Refer to the exhibit, which contains a session diagnostic output.
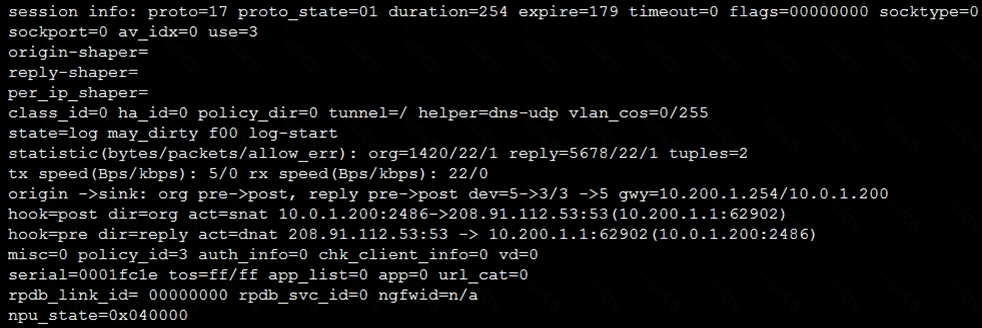
Which statement is true about the session diagnostic output?
Which two statements explain antivirus scanning modes? (Choose two.)
109
Why does FortiGate keep TCP sessions in the session table for some seconds even after both sides
(client and server) have terminated the session?
20
Which two statements are true about the RPF check? (Choose two.)
Refer to the exhibit.
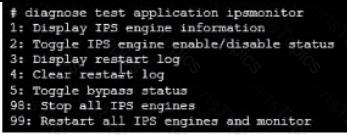
Examine the intrusion prevention system (IPS) diagnostic command.
Which statement is correct If option 5 was used with the IPS diagnostic command and the outcome was a decrease in the CPU usage?
Refer to the exhibits.
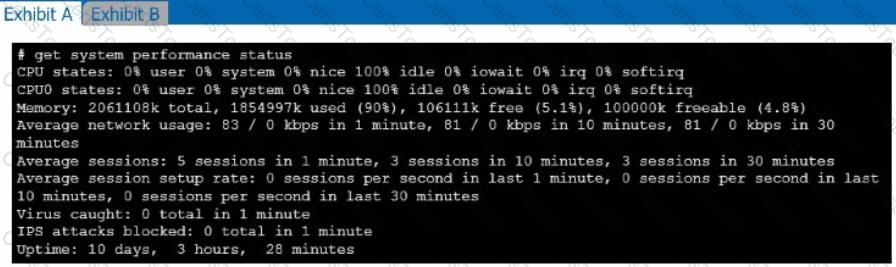
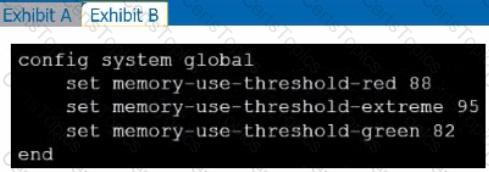
Exhibit A shows system performance output. Exhibit B shows a FortiGate configured with the default configuration of high memory usage thresholds. Based on the system performance output, which two statements are correct? (Choose two.)
Refer to the exhibit.

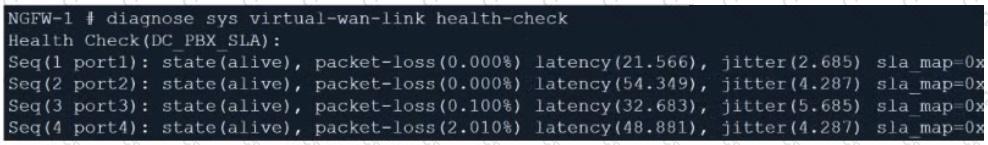
The exhibit contains the configuration for an SD-WAN Performance SLA, as well as the output of diagnose sys virtual-wan-link health-check . Which interface will be selected as an outgoing interface?
82
Consider the topology:
Application on a Windows machine <--{SSL VPN} -->FGT--> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server. This issue does not happen when the application establishes a Telnet connection to the Linux server directly on the LAN.
What two changes can the administrator make to resolve the issue without affecting services running through FortiGate? (Choose two.)
Which two statements are correct regarding FortiGate FSSO agentless polling mode? (Choose two.)
View the exhibit.
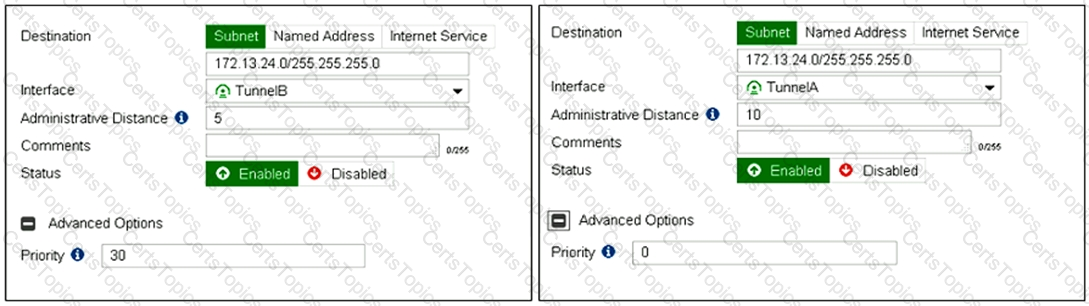
Which of the following statements are correct? (Choose two.)
Refer to the exhibit.
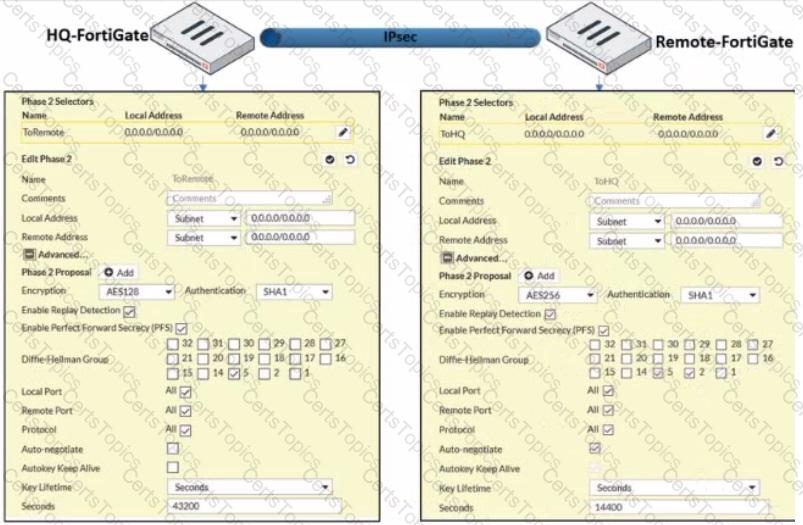
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 status is up. but phase 2 fails to come up.
Based on the phase 2 configuration shown in the exhibit, what configuration change will bring phase 2 up?
Refer to the exhibits.
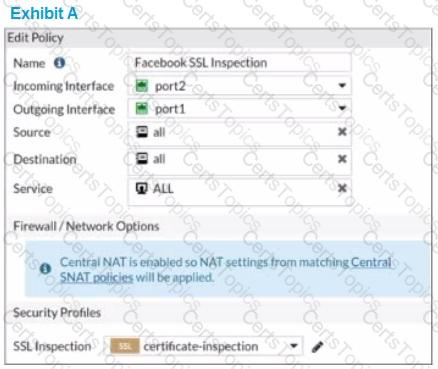
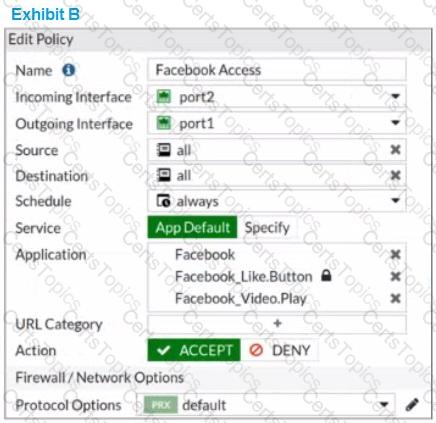
The exhibits show the SSL and authentication policy (Exhibit A) and the security policy (Exhibit B) for Facebook .
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the policy configuration must you change to resolve the issue?
Which two configuration settings are synchronized when FortiGate devices are in an active-active HA cluster? (Choose two.)
Refer to the exhibit.
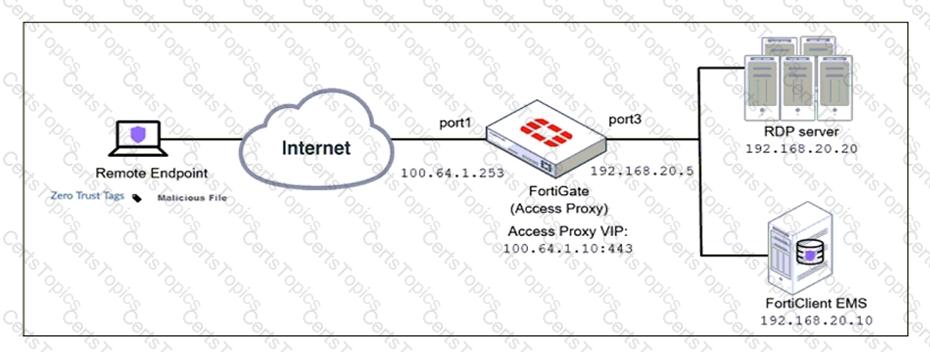
Based on the ZTNA tag, the security posture of the remote endpoint has changed.
What will happen to endpoint active ZTNA sessions?
34
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile. What order must FortiGate use when the web filter profile has features enabled, such as safe search?
Which statement describes a characteristic of automation stitches?
43
Which two statements are correct about SLA targets? (Choose two.)
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
Refer to the exhibits.
The exhibits show a network diagram and firewall configurations.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2. Remote-User1 must be able to access the Webserver. Remote-User2 must not be able to access the Webserver.
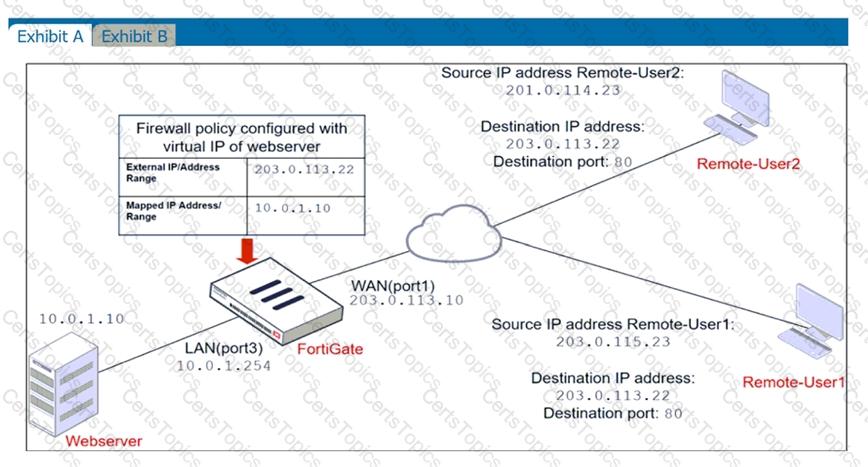
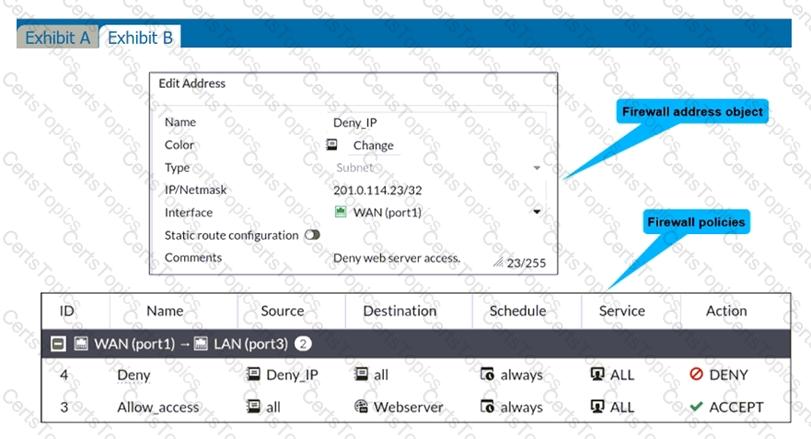
In this scenario, which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose two.)
84
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
Which two statements about FortiGate FSSO agentless polling mode are true? (Choose two.)
17
In consolidated firewall policies, IPv4 and IPv6 policies are combined in a single consolidated policy. Instead of separate policies. Which three statements are true about consolidated IPv4 and IPv6 policy configuration? (Choose three.)
Which scanning technique on FortiGate can be enabled only on the CLI?