Which two purposes is the dedicated IP address used for in a FortiSASE deployment? (Choose two.)
What is the recommended method to upgrade FortiClient in a FortiSASE deployment?
Which two settings are automatically pushed from FortiSASE to FortiClient in a new FortiSASE deployment with default settings? (Choose two.)
Refer to the exhibits.
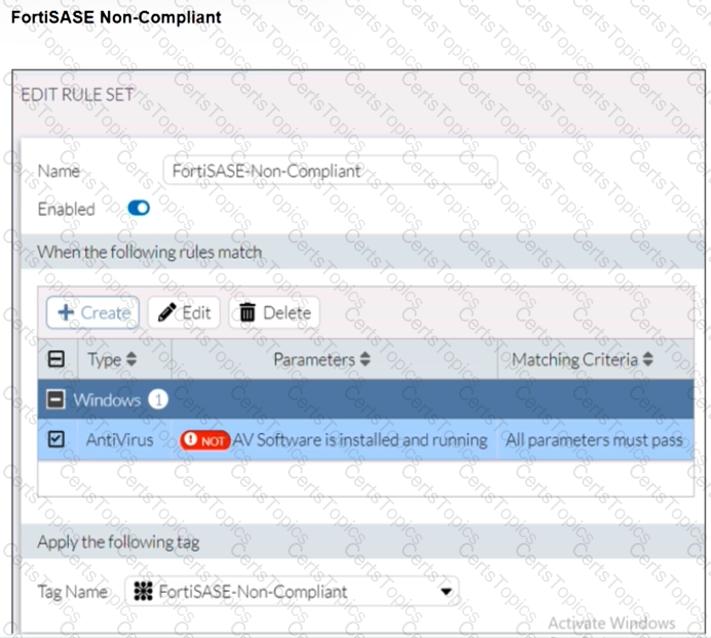
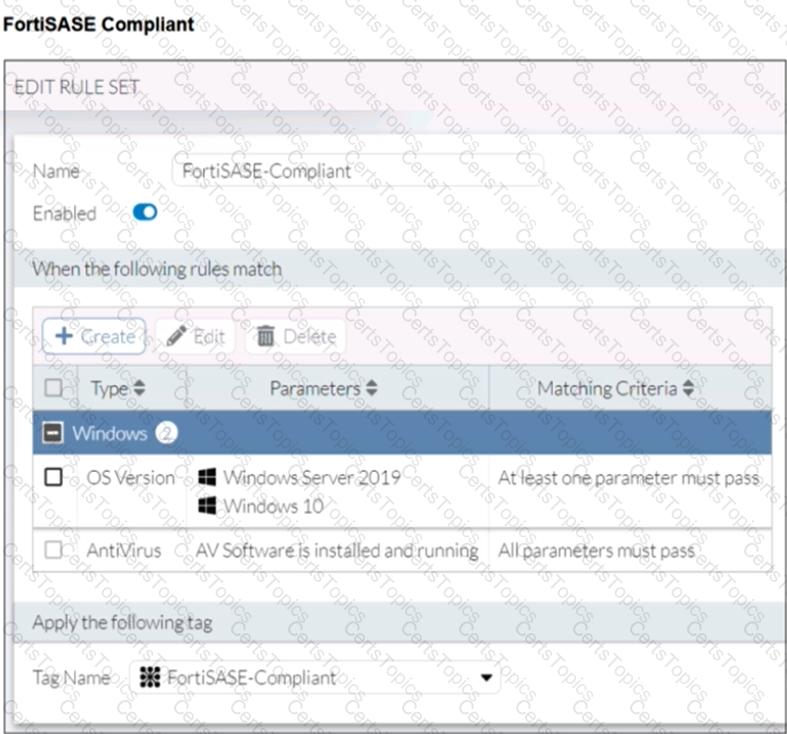
Antivirus is installed on a Windows 10 endpoint, but the windows application firewall is stopping it from running.
What will the endpoint security posture check be?
For monitoring potentially unwanted applications on endpoints, which information is available on the FortiSASE software installations page?
Which FortiSASE feature ensures least-privileged user access to corporate applications that are protected by an on-premises FortiGate device?
Which two additional features does FortiClient integration provide with FortiSASE, when compared to secure web gateway (SWG) deployment? (Choose two.)
How does FortiSASE hide user information when viewing and analyzing logs?
What can be configured on FortiSASE as an additional layer of security for FortiClient registration?
Refer to the exhibits.

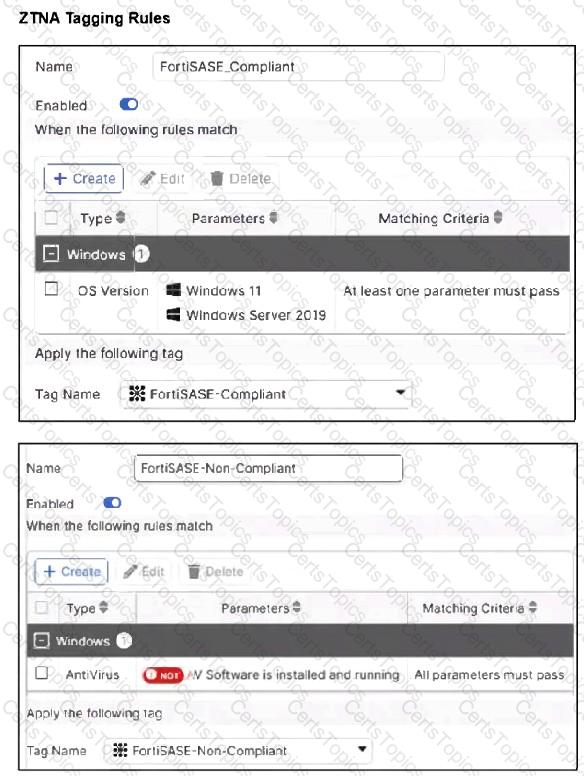
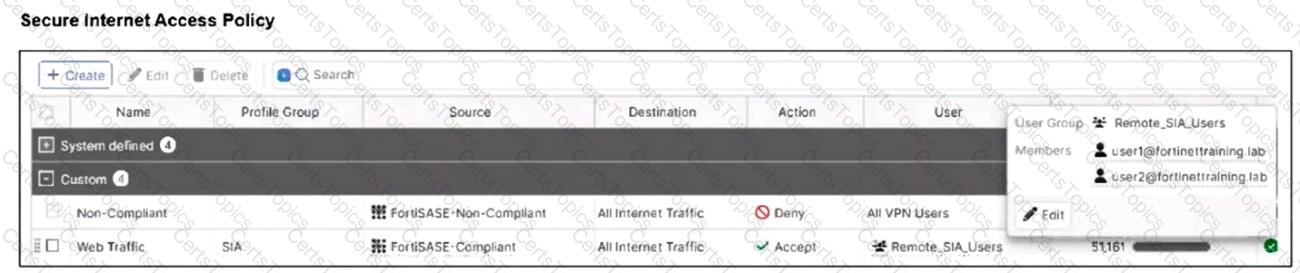
Jumpbox and Windows-AD are endpoints from the same remote location. Jumpbox can access the internet through FortiSASE, while Windows-AD can no longer access the internet.
Based on the information in the exhibits, which reason explains the outage on Windows-AD?
Refer to the exhibits.




A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub.
Based on the exhibits, what is the reason for the access failure?
Which information does FortiSASE use to bring network lockdown into effect on an endpoint?
Refer to the exhibits.
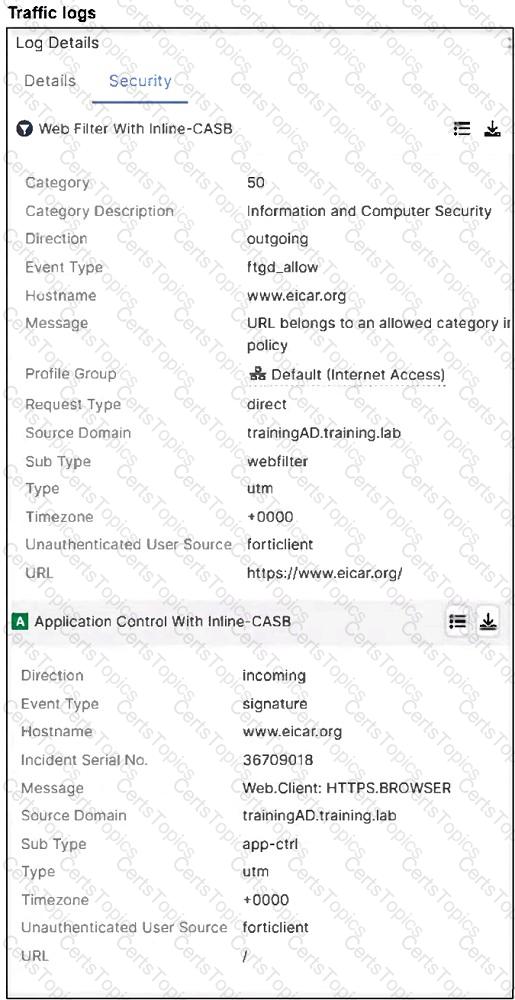
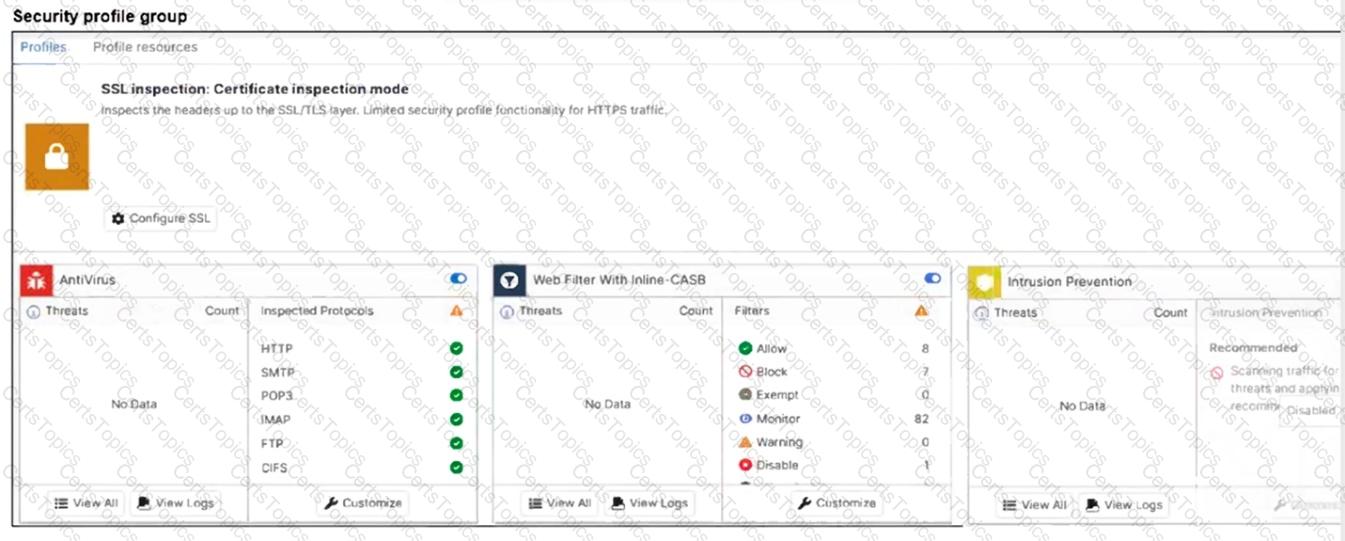
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from
Which configuration on FortiSASE is allowing users to perform the download?
In a FortiSASE secure web gateway (SWG) deployment, which two features protect against web-based threats? (Choose two.)
In the Secure Private Access (SPA) use case, which two FortiSASE features facilitate access to corporate applications? (Choose two.)