An administrator would like to use FortiCNP to keep track ofsensitive data files located in the Amazon Web Services (AWS) S3bucket and protect it from malware. Which FortiCNP feature should the administrator use?
You must add an Amazon Web Services (AWS) network access list (NACL) rule to allow SSH traffic to a subnet for temporary testing purposes. When you review the current inbound and outbound NACL rules, you notice that the rules with number 5 deny SSH and telnet traffic to the subnet.
What can you do to allow SSH traffic?
Which statement about Transit Gateway (TGW) in Amazon Web Services (AWS) is true?
You have deployed a FortiGate HA cluster in Azure using a gateway load balancer for traffic inspection. However, traffic is not being routed correctly through the firewalls.
What can be the cause of the issue?
Refer to the exhibit.
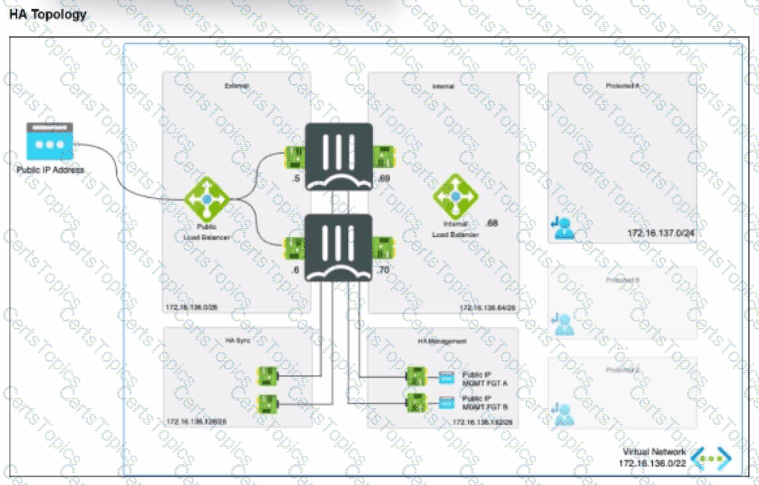
The exhibit shows an active-passive high availability FortiGate pair with external and internal Azure load balancers There is no SDN connector used in this solution.
Which configuration must the administrator implement on each FortiGate?
Refer to the exhibit.

You are troubleshooting a Microsoft Azure SDN connector issue on your FortiGate VM in Azure.
Which command can you use to examine details about API calls sent by the connector?
As part of your organization's monitoring plan, you have been tasked with obtaining and analyzing detailed information about the traffic sourced at one of your FortiGate EC2 instances.
What can you do to achieve this goal?
Refer to the exhibit.
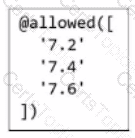
What is the purpose of this section of an Azure Bicep file?
Refer to the exhibit.
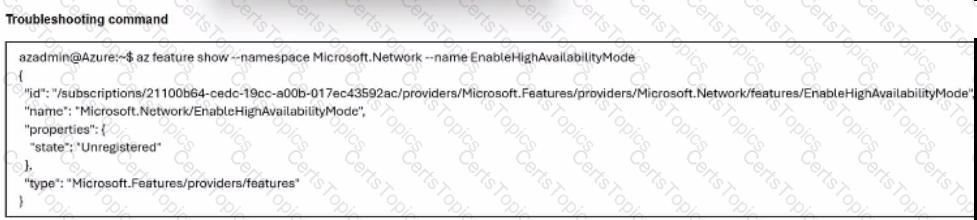
A managed security service provider (MSSP) administration team is trying to deploy a new HA cluster in Azure to filter traffic to and from a client that is also using Azure. However, every deployment attempt fails, and only some of the resources are deployed successfully. While troubleshooting this issue, the team runs the command shown in the exhibit.
What are the implications of the output of the command?
Your DevOps team is evaluating different Infrastructure as Code (IaC) solutions for deploying complex Azure environments.
What is an advantage of choosing Azure Bicep over other IaC tools available?
You need a solution to safeguard public cloud-hosted web applications from the OWASP Top 10 vulnerabilities. The solution must support the same region in which your applications reside, with minimum traffic cost.
Which solution meets the requirements?