Question:
What information is available in a capacity planning report for storage infrastructure?
Question:
What is the maximum number of VLANs that can be supported with one VLAN tag field?
Question:
What is true about the FCIP?
Question:
How does Storage Class Memory (SCM) compare to DRAM and flash memory in terms of speed?
Question:
What is an advantage of deploying intelligent storage systems in the data center?
Question:
An Ethernet switch has eight ports, and all ports must be operational for 24 hours from Monday through Friday. However, failures of Port 6 occur within the week as follows:
Tuesday: 6 AM to 8 AM
Thursday: 5 PM to 10 PM
Friday: 7 AM to 9 AMWhat is the MTBF (Mean Time Between Failures) of Port 6?
Question:
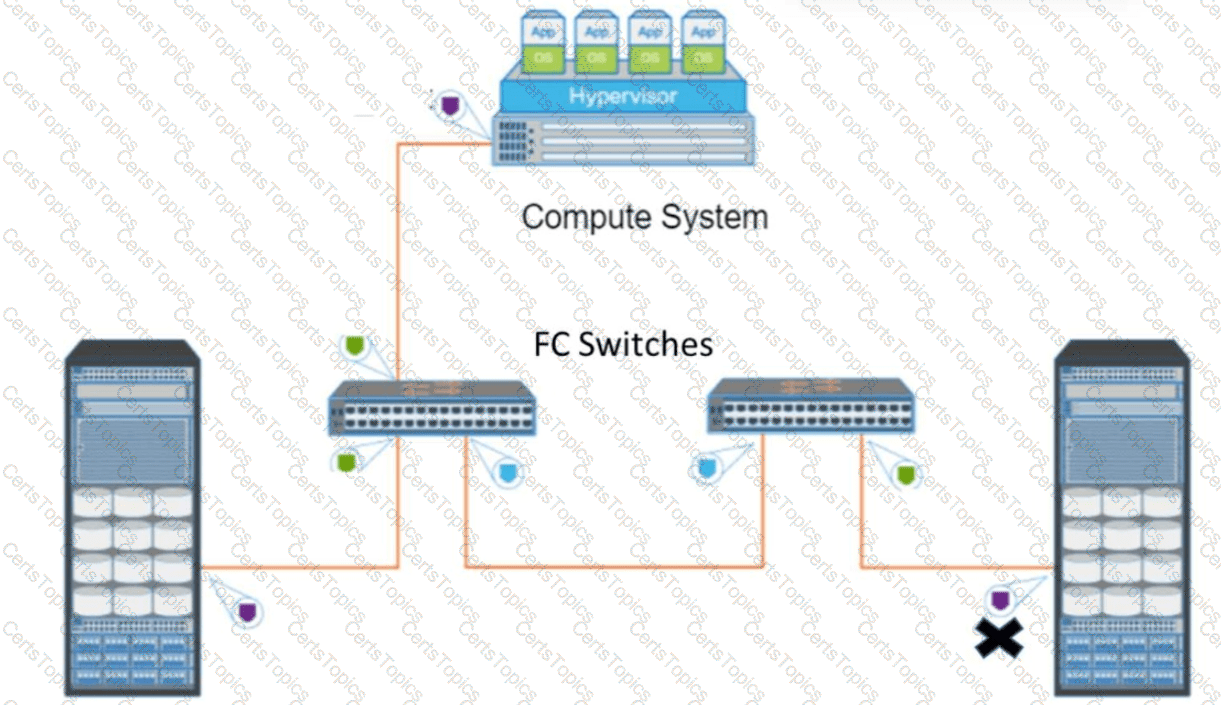
Refer to the Exhibit (Port marked "X"): What type of FC port does the "X" represent?
Question:
What is the role of the storage node in a backup architecture?
Question:
A backup array was able to achieve a 30:1 reduction by finding multiple copies of the same data. Which method was used in this scenario?
Question:
When troubleshooting a virtual machine, which file is most likely to provide a detailed history of the VM's behavior?
Question:
What type of disk devices are the highest performing and most expensive of all disk devices?
Question:
What is the function of a continuous data protection (CDP) appliance?
Question:
What describes an incident in a storage infrastructure?
Question:
A storage administrator needs to track the performance and availability of storage components and services. Which storage management function would provide this information?
Question:
What is a read miss in cache operations?
Question:
What is the main advantage of Network Attached Storage (NAS) systems over general-purpose servers?
Question:
An IT department needs to execute automated tasks to perform a business operation. They require workflows for arranging, coordinating, and managing these tasks. Which layer of the Modern Data Center Architecture provides this functionality?
Question:
A company is implementing a new information security policy. They want to ensure that the policy aligns with its risk appetite, internal policies, and external regulations. Which framework can help the company achieve this goal?