When a Cisco WSA is installed with default settings, which port is assigned to the web proxy if the M1 port is used exclusively for management?
Which behavior is seen while the policy trace tool is used to troubleshoot a Cisco WSA?
Which key is needed to pair a Cisco WSA and Cisco ScanCenter for CTA?
When an access policy is created, what is the default option for the Application Settings?
Which type of certificate must be installed on a Cisco WSA for HTTPS inspection?
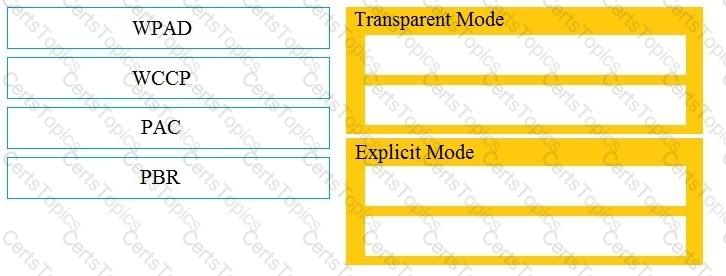
Drag and drop the Cisco WSA methods from the left onto the correct deployment modes on the right.
Refer to the exhibit.
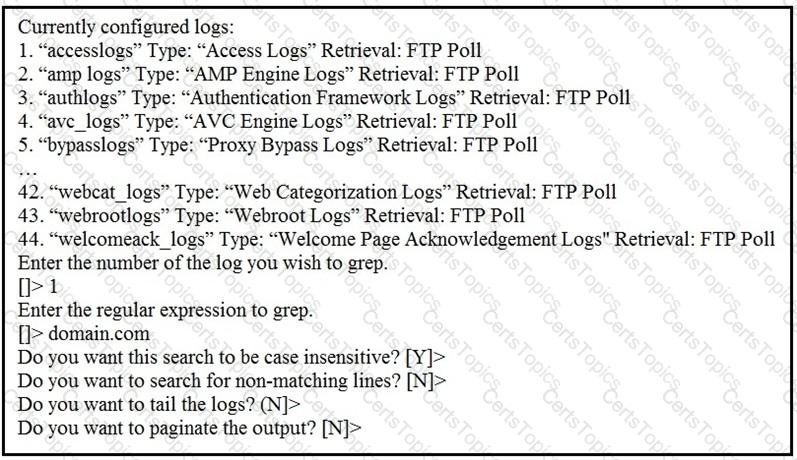
Which command displays this output?
Which statement about Cisco Advanced Web Security Reporting integration is true?
Which response code in the access logs indicates that a transaction was blocked due to policy?