An administrator needs to configure Cisco ESA to ensure that emails are sent and authorized by the owner of the domain. Which two steps must be performed to accomplish this task? (Choose two.)
Which functionality is impacted if the assigned certificate under one of the IP interfaces is modified?
Which of the following two steps are required to enable Cisco SecureX integration on a Cisco Secure Email Gateway appliance? (Choose two.)
Which two actions are configured on the Cisco ESA to query LDAP servers? (Choose two.)
Which components are required when encrypting SMTP with TLS on a Cisco Secure Email Gateway appliance when the sender requires TLS verification?
An engineer wants to utilize a digital signature in outgoing emails to validate to others that the email they are receiving was indeed sent and authorized by the owner of that domain Which two components should be configured on the Cisco Secure Email Gateway appliance to achieve this? (Choose two.)
An organization has a strict policy on URLs embedded in emails. The policy allows visibility into what the URL is but does not allow the user to click it. Which action must be taken to meet the requirements of the security policy?
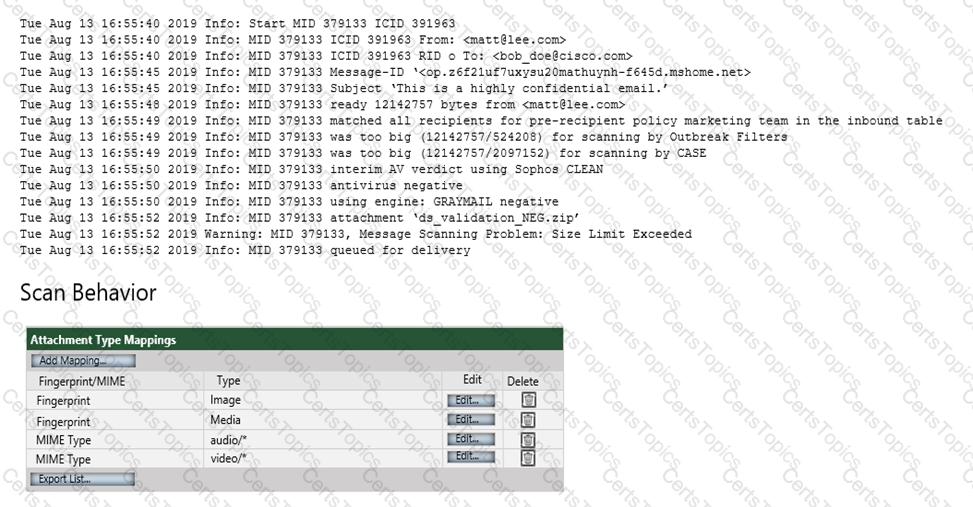
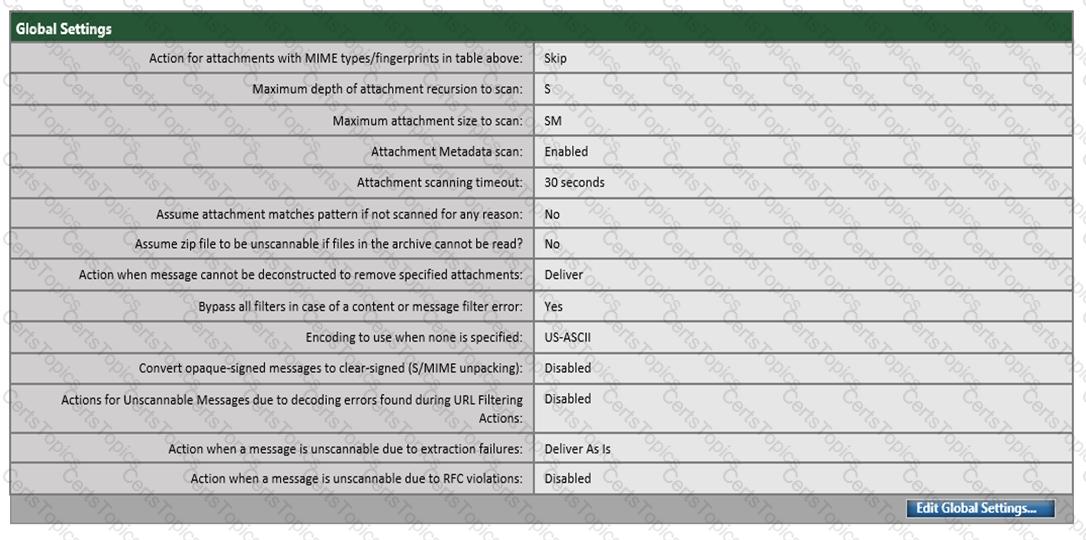
Refer to the exhibit. Which configuration on the scan behavior must be updated to allow the attachment to be scanned on the Cisco ESA?
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
The company security policy requires that the finance department have an easy way to apply encryption to their outbound messages that contain sensitive data Users must be able to flag the messages that require encryption versus a Cisco Secure Email Gateway appliance scanning all messages and automatically encrypting via detection Which action enables this capability?
What are two primary components of content filters? (Choose two.)
What is the purpose of Cisco Email Encryption on Cisco ESA?
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
Which two features are applied to either incoming or outgoing mail policies? (Choose two.)
What are two phases of the Cisco ESA email pipeline? (Choose two.)
When outbreak filters are configured, which two actions are used to protect users from outbreaks? (Choose two.)
Which Cisco ESA security service is configured only through an outgoing mail policy?
Which Cisco Secure Email Threat Defense visibility and remediation mode is only available when using Cisco Secure Email Gateway as the message source?
Which component must be added to the content filter to trigger on failed SPF Verification or DKIM Authentication verdicts?
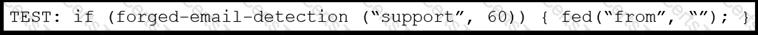
Refer to the exhibit. An engineer needs to change the existing Forged Email Detection message filter so that it references a newly created dictionary named ‘Executives’.
What should be done to accomplish this task?
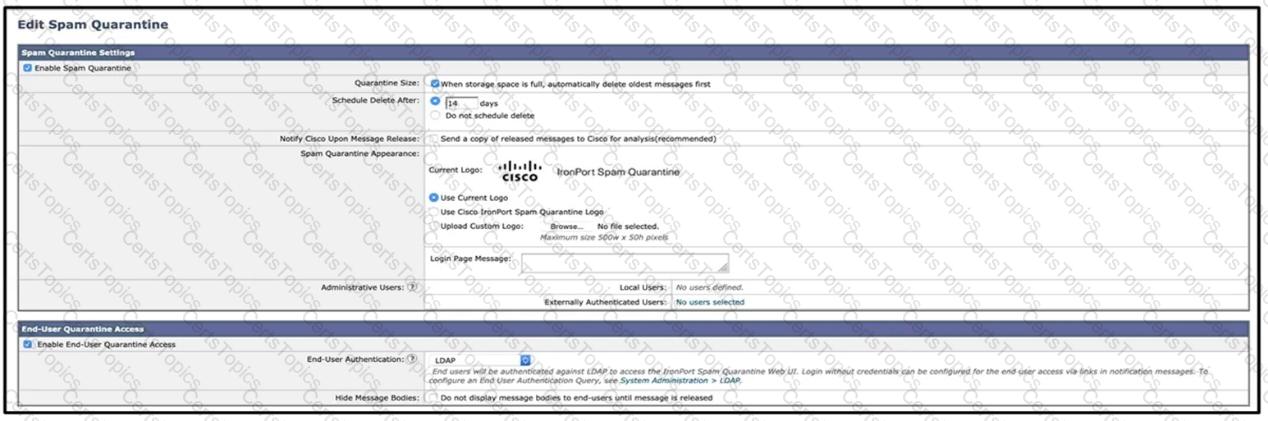

Refer to the exhibits. What must be done to enforce end user authentication before accessing quarantine?
When the spam quarantine is configured on the Cisco Secure Email Gateway, which type of query is used to validate non administrative user access to the end-user quarantine via LDAP?
Email encryption is configured on a Cisco ESA that uses CRES.
Which action is taken on a message when CRES is unavailable?
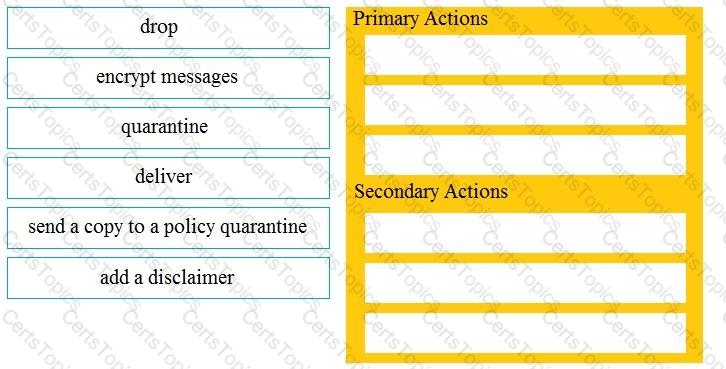
Drag and drop the Cisco ESA reactions to a possible DLP from the left onto the correct action types on the right.
Which feature utilizes sensor information obtained from Talos intelligence to filter email servers connecting into the Cisco ESA?
An engineer deploys a Cisco Secure Email Gateway appliance with default settings in an organization that permits only standard H feature does not work. Which additional action resolves the issue?
When outbreak filters are configured, which two actions are used to protect users from outbreaks? (Choose two.)
What is the default HTTPS port when configuring spam quarantine on Cisco ESA?
Refer to the exhibit.
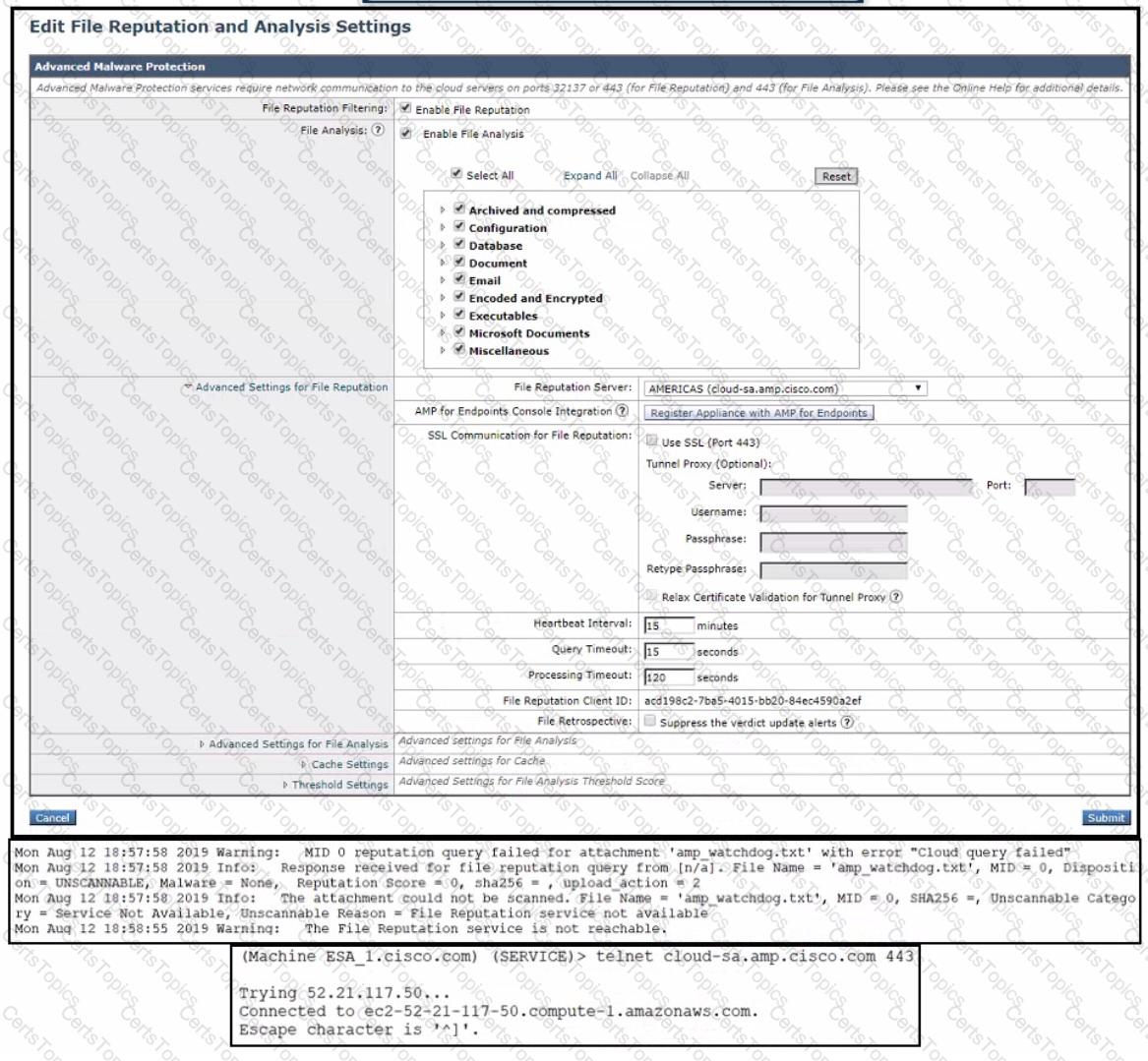
An administrator has configured File Reputation and File Analysis on the Cisco Secure Email Gateway appliance however it does not function as expected What must be configured on the appliance for this to function?
An engineer tries to implement phishing simul-ations to test end users, but they are being blocked by the Cisco Secure Email Gateway appliance. Which two components, when added to the allow list, allow these simul-ations to bypass antispam scanning? (Choose two.)
Refer to the exhibit.

Which SPF record is valid for mycompany.com?
Email encryption is configured on a Cisco ESA that uses CRES.
Which action is taken on a message when CRES is unavailable?
Refer to the exhibit.
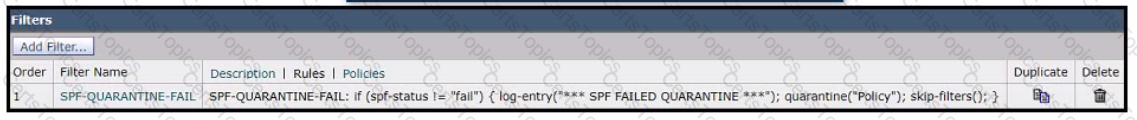
A network engineer must set up a content filter to find any messages that failed SPF and send them into quarantine The content filter has been set up and enabled, but all messages except those that have failed SPF are being sent into quarantine. Which section of the filter must be modified to correct this behavior?
Which process is skipped when an email is received from safedomain.com, which is on the safelist?
What are organizations trying to address when implementing a SPAM quarantine?
What must be configured to allow the Cisco ESA to encrypt an email using the Cisco Registered Envelope Service?
Which method enables an engineer to deliver a flagged message to a specific virtual gateway address in the most flexible way?
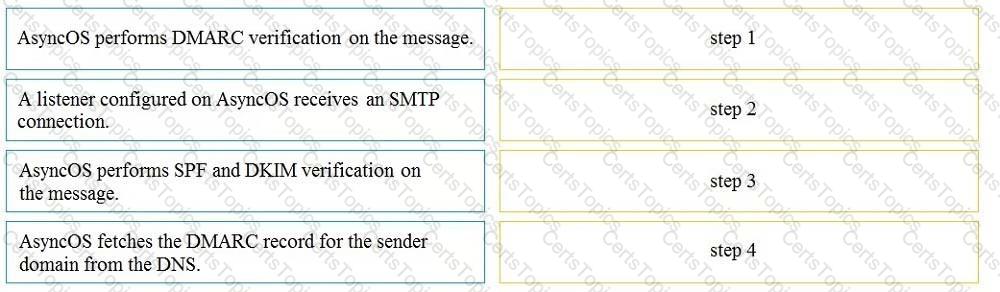
Drag and drop the AsyncOS methods for performing DMARC verification from the left into the correct order on the right.
When the Cisco ESA is configured to perform antivirus scanning, what is the default timeout value?
Which setting affects the aggressiveness of spam detection?
What is the default port to deliver emails from the Cisco ESA to the Cisco SMA using the centralized Spam Quarantine?
When the Spam Quarantine is configured on the Cisco ESA, what validates end-users via LDAP during login to the End-User Quarantine?
When the Spam Quarantine is configured on the Cisco ESA, what validates end-users via LDAP during login to the End-User Quarantine?
A Cisco Secure Email Gateway appliance is processing many messages that are sent to invalid recipients verification. Which two steps are required to accomplish this task? (Choose two.)